The Challenge
Helix, the embedded-finance platform from Q2, provides the cloud-native banking infrastructure that powers modern fintech innovation. It enables fintechs, consumer brands, and technology companies to embed financial products such as accounts, payments, and virtual or physical cards, directly into their applications, while connecting them with chartered financial institutions that manage deposits and regulatory oversight.
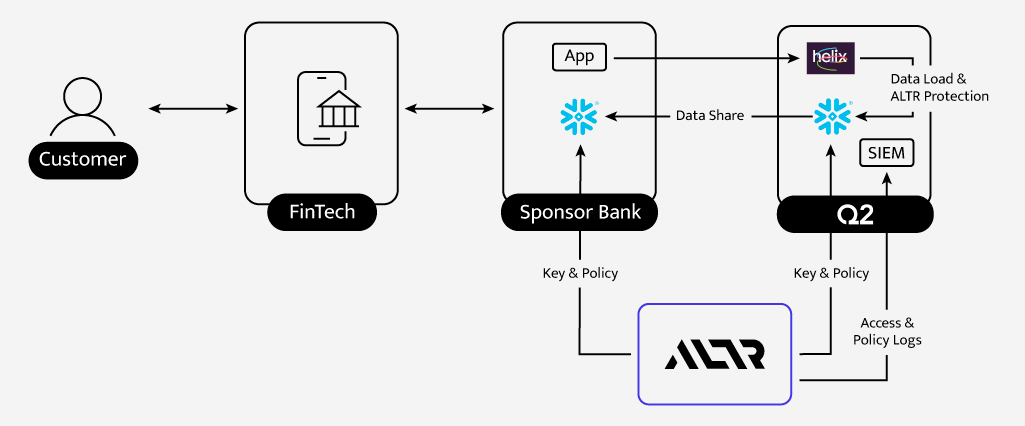
One of the largest fintech programs on the Helix platform began scaling rapidly, supporting millions of customer accounts and transactions between a leading fintech and its partner bank. To deliver shared visibility into this data, both the fintech and the bank needed secure, policy-driven access to information hosted in Snowflake without exposing each other’s customer data or compromising compliance requirements.
The challenge was clear:
- Enable secure collaboration between the fintech, its partner bank, and the Helix platform.
- Partition data cryptographically so that each party can see only its own records.
- Maintain performance and usability for analytics in Snowflake.
Traditional database controls and cryptographic mechanisms weren’t built for this kind of multi-party, real-time data ecosystem, where data accessibility, governance, and scale must coexist.
The Solution
To secure sensitive financial data shared between the fintech, its banking partner, and Q2 Helix, ALTR applied its Format-Preserving Encryption (FPE) and Advanced Encryption Standard (AES) together with fine-grained policy enforcement and centralized key management; all operating natively within Snowflake to protect data and control access at scale.
As a Snowflake Premier Partner designated with the Snowflake Financial Services Competency badge, ALTR is recognized for its proven expertise in data control and security within the Snowflake Financial Services Data Cloud, making it uniquely qualified to support complex, regulated use cases like this one.
While Snowflake provides strong native controls for data sharing and governance, it’s only with ALTR that complete security, compliance, and policy enforcement become seamless. ALTR extends Snowflake’s capabilities ensuring every layer of data protection operates automatically and consistently.
Cost is always a factor when it comes to large Snowflake workloads. ALTR’s Snowflake-native approach is designed with this in mind, optimizing performance and ensuring Q2 and its partners receive maximum value for every Snowflake credit consumed during operations.
Data Protection with FPE
Helix’s shared data model includes highly sensitive fields such as account identifiers, balances, and transactions, used across multiple applications and analytics pipelines. FPE is used selectively to prevent broken schemas, indexes, and queries, forcing costly code changes. AES was used where format was not required and performance was the highest priority.
ALTR’s Snowflake-native encryption solution eliminates those tradeoffs by encrypting data while preserving its original format and structure. This allows Helix and its partners to:
- Maintain full compatibility with existing schemas and application logic.
- Run SQL queries and joins without modification.
- Preserve performance with AES for large-scale analytical workloads.
Encrypted fields remain statistically valid and structurally intact, enabling secure computation and reporting across massive datasets without compromising usability.
Policy Enforcement and Key Management
Every protected data field is governed by an ALTR policy defining who can access it, how, and under what conditions. Policies are centrally managed and automatically enforced inside Snowflake, giving Q2 or its partners full control over:
- Granularity: Row-, column-, or field-level access precision.
- Delegation: Ensuring each fintech and bank can decrypt only its own datasets.
- Auditability: Real-time logging of every key usage and data access event.
The data is encrypted in a cryptographically isolated manner, ensuring each fintech and bank can only decrypt its own datasets. ALTR customers also have the ability to provide their own key management solutions further increasing control and security.
When data is shared through Snowflake’s native data-sharing, ALTR ensures:
- Keys are delivered securely and scoped only to authorized entities.
- No plaintext ever leaves the controlled environment.
- Even when datasets are shared broadly, only the rightful owner can decrypt their portion.
This architecture gives Helix and its partners real-time analytical visibility across millions of customer records, with data continuously updated every hour around the clock. ALTR’s policies and key management ensure that every update remains governed, encrypted, and isolated by design.
The Result
- End-to-end data protection: Millions of customer records are now governed by ALTR’s encrypted and policy-controlled framework in production.
- Real-time, governed visibility: Data is refreshed every hour, giving Helix and its partners real-time insight into activity while ALTR ensures each participant can access only the data they’re authorized to see, no cross-tenant exposure, ever.
- Format-preserving performance: FPE maintains data integrity and analytics speed across Helix’s shared model, while AES delivers high-performance protection for fields where format preservation isn’t required.
- Seamless data sharing: ALTR’s key management integrates with Snowflake’s native data-sharing to ensure privacy and compliance.
- Operational efficiency: ALTR’s Snowflake-native design optimizes query performance and resource use, ensuring maximum value of Snowflake
- Enterprise scale: The solution supports large, regulated embedded-finance operations without adding friction to innovation.
By combining Helix’s embedded-finance architecture with ALTR’s Format-Preserving Encryption and policy-based access control, Q2 enabled its fintech and banking partners to share and analyze sensitive data securely—at the scale of millions of customers.
The result is a governed data ecosystem where performance, compliance, and security all operate in harmony, proving that data sharing and data protection can coexist by design.