In today’s data-driven economy, companies are juggling an impossible paradox: democratize access to data while locking it down tighter than ever. Business units demand faster access to insights, developers need data for testing, and partners often need a peek under the hood. But every query, download, and access request opens a new window for something to go very wrong, very fast.
That is where Database Activity Monitoring (DAM) comes in. If your data security strategy does not include a DAM solution, you are flying blind.
What Is Database Activity Monitoring?
Database Activity Monitoring is exactly what it sounds like: a way to continuously monitor and record database activity, especially access to sensitive data. But a strong DAM solution does more than just log activity. It answers the critical security questions in real time:
- Who is accessing the data?
- What are they accessing?
- When are they doing it?
- Is this typical, or is something suspicious happening?
DAM provides visibility into your organization’s most sensitive assets and enables you to enforce policies that keep your business secure, compliant, and resilient.
>>> You Might Also Like: The Fastest DAM Way to Improve Security in Snowflake
Why You Need Database Activity Monitoring
Perimeter Defenses Are Not Enough
You can build the world’s best firewall, but it will not catch a rogue insider pulling sensitive data at 2 a.m. DAM works inside your environment, directly at the database layer, where real threats originate.
Audit Trails Are Non-Negotiable
When compliance officers ask for documentation, you need more than a general sense of what happened. DAM provides detailed, tamper-proof logs showing exactly who accessed what, when, and how.
>>> You Might Also Like: Why Query Audit Logs are Critical for Security & Compliance
Threats Are Not Always Obvious
A gradual leak of 10,000 records per hour might seem normal on the surface. But DAM can detect access patterns, rate anomalies, and usage spikes that would otherwise go unnoticed.
Speed Is Everything
When something goes wrong, minutes matter. DAM allows your security team to detect and contain threats immediately, not days or weeks later.
Common Use Cases Across Industries
Database Activity Monitoring is not industry-specific. It solves universal problems related to data visibility, misuse, and compliance. Here is how various industries rely on DAM to stay secure and audit-ready:
Financial Services
Monitoring access to account numbers, credit records, and transaction data helps institutions meet PCI DSS, SOX, and GLBA compliance requirements while protecting against insider fraud.
Healthcare
Hospitals and providers use DAM to protect protected health information (PHI), track user access, and maintain HIPAA compliance. It also helps spot unauthorized snooping or excessive access to patient records.
Retail and eCommerce
Retailers use DAM to protect customer PII and payment data, particularly during peak sales seasons when traffic spikes and attackers look to exploit overlooked vulnerabilities.
SaaS and Technology Companies
Tech firms use DAM to track developer activity, monitor third-party access to production environments, and maintain visibility into how internal teams handle sensitive IP and customer data.
What Happens Without It? (Life Without DAM)
If you are not monitoring database activity, you are operating on assumptions and leaving the door open to significant risk. Without DAM:
Breach Detection Is Delayed
Many data breaches go undetected for weeks or months. Without real-time insights, attackers have time to move laterally, escalate privileges, and extract data unnoticed.
Audit and Compliance Responses Are Slow and Incomplete
When your audit team needs documentation, manual data gathering wastes time and leaves gaps. DAM delivers structured, exportable logs that satisfy even the most stringent compliance checks.
Insider Threats Go Undetected
Not all data leaks come from outside the organization. Employees with elevated access can do damage without anyone noticing unless their activity is monitored in real time.
Anomalous Behavior Blends In
Excessive access, strange timing, or usage from unexpected locations often go unnoticed without rules-based alerting tied to actual usage baselines.
ALTR: Elevating DAM from Passive Monitoring to Active Defense
Most DAM solutions take a passive approach. They collect logs, generate reports, and occasionally trigger alerts. ALTR redefines what is possible by putting monitoring, analytics, and protection into a single intelligent platform.
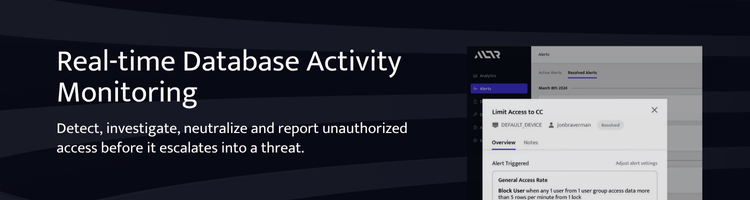
Near-Real-Time Detection and Response
ALTR continuously monitors access to sensitive data and enables customers to define precise rules for expected behavior. If those rules are violated, ALTR does not just alert you—it can block access immediately. Whether it is an unusually large query, an access attempt at an odd hour, or activity from an unexpected role, ALTR is built to detect and disrupt potential threats as they happen.
Data Classification and Discovery
Effective monitoring starts with knowing what to protect. ALTR automatically classifies data as sensitive or non-sensitive, allowing you to create customized policies based on the nature and context of each dataset. This removes guesswork and ensures your highest-risk data gets the strongest safeguards.
Data Usage Analytics and Visualization
With ALTR, you gain a clear picture of how users interact with data across time. The platform tracks who is accessing what, how often, and when, surfacing trends and deviations. Security teams can compare current behavior to historical baselines to identify anomalies, misuse, or emerging risks—whether or not a breach has occurred.
Fine-Grained Access Control Policies
ALTR’s policy engine enables you to set highly specific boundaries: users can be limited by role, time of day, volume of data, or types of queries. These controls go beyond basic permissions and give organizations the power to proactively define safe data behavior.
Customizable Events and Alerting
ALTR allows security teams to tailor alerting thresholds and responses to meet the unique needs of the business. Whether you want alerts on access attempts outside business hours or automated blocks for data transfers above a certain size, ALTR adapts to your risk posture.
Integration with SIEM and Security Operations
ALTR does not require you to rip and replace your existing security stack. It exports audit and activity logs in near real time, feeding data into your SIEM or security data lake so your SOC team can act without delay.
End-to-End Auditing, Including Itself
Unlike most tools, ALTR also audits its own configuration and activity. Any changes to its settings or policy framework are logged, so security leaders can verify that no unauthorized modifications have occurred—even within the platform itself.
Tokenization and Encryption Activity Logging
For customers using ALTR’s advanced data protection tools, such as tokenization and format-preserving encryption, ALTR generates separate logs for each tokenization or detokenization event. These logs include who performed the operation, when it occurred, and the amount of data involved, offering a complete view of how sensitive information is accessed and protected.
ALTR is not just another security tool—it is the command center for enforcing your data security and access policies with precision and accountability.
Wrapping Up
In a world where a single query can expose millions of records, database activity monitoring is no longer a nice-to-have. It is a business necessity. You cannot protect what you cannot see. And you certainly cannot respond to threats you never even knew existed.
ALTR makes the invisible visible. It delivers not only observability but accountability, with built-in enforcement and real-time protection that turn data risk into data resilience.
Ready to See It in Action?
Do not wait for a breach to highlight the gap. Schedule a product tour and see how database activity monitoring should really be done.
Key Takeways
- Database Activity Monitoring (DAM) provides real-time visibility into who is accessing your data, what they are accessing, and when.
- DAM is essential for protecting sensitive data, identifying insider threats, and meeting compliance requirements like HIPAA, PCI DSS, and GDPR.
- Traditional security tools fall short at the database level—DAM fills the visibility gap and enables proactive response to threats.
- Without DAM, organizations face delayed breach detection, poor audit readiness, and lack of insight into anomalous or excessive access.
- Effective DAM solutions go beyond logging, offering data classification, policy-based access control, anomaly detection, and security integration.
- Real-time alerting and enforcement capabilities are critical to stopping unauthorized access before it causes damage.
- A strong DAM platform supports SIEM integration, customizable policies, and rich analytics to streamline threat detection and compliance efforts.