How to Set Effective Security Thresholds for Your Data
Data security isn’t just about stopping hackers at the gates—it’s about knowing what’s happening inside your systems at all times. As organizations collect, store, and analyze more data than ever before, keeping sensitive information secure requires more than encryption or firewalls. It demands active monitoring and the enforcement of thresholds that ensure data is accessed appropriately and responsibly.
But how do you determine the right thresholds for your organization? How can you enforce these thresholds effectively? And most importantly, what should you do when a threshold is breached? In this blog, we’ll explore the answers to these questions and provide actionable guidance for setting security thresholds tailored to your organization’s needs.
What Is a Security Threshold?
Before diving into the details, let’s start with the basics. A threshold is a rule or policy designed to limit or monitor access to data based on predefined parameters. Thresholds are not just about protecting data; they’re about ensuring data is used in ways that align with organizational goals, roles, and compliance requirements.
ALTR’s Thresholding Feature
ALTR’s Thresholding feature takes data security to the next level by enabling policies that go beyond traditional column-, tag-, or row-based protections. It allows you to define actions and rules that govern data access and usage, creating a dynamic layer of control that responds to real-time activity.
Actions
- Block: A single user is blocked from accessing ALTR-protected data, and an alert is created.
- Alert Only: An alert is generated for the specific access that was attempted.
Rules
- Access Rate: A user can query a specific number of rows of data within a specific time range (minute, hour, day, month, year).
- Time Window: A user can query during specific days of the week, between specific times of day.
For example, let’s say your organization’s Customer Support Analysts typically help up to 5 customers per hour. To maintain security, you could implement the following thresholds:
Alerting Threshold: When a Customer Support Analyst accesses 6–10 rows of customer data in an hour, an alert is triggered. This helps identify unusual activity without disrupting operations.
Blocking Threshold: If access exceeds 15–20 rows of customer data in an hour, the system blocks further queries and generates an alert, ensuring sensitive information is not compromised.
These thresholds not only prevent misuse but also provide actionable insights into your data usage patterns.
Making Informed Decisions with ALTR’s Data Insights
To enforce effective thresholds, you need to understand how your data is being used. ALTR generates rich, real-time data that provides full visibility into sensitive data activity. Here’s how ALTR equips you with the insights needed to make informed decisions:
Query Audits
Every time a user queries ALTR-protected data, an audit is created. This real-time log includes details such as:
- Who performed the query
- What query was executed
- When it occurred
- How much data was returned
Threshold Breach Alerts
When a threshold is breached, ALTR generates an alert detailing:
- Who breached the threshold
- What threshold was violated
- The exact query that caused the breach
With this granular data, you can pinpoint issues quickly and act decisively.
How to Use ALTR-generated Data
ALTR-generated data is exported in real time to a customer-managed S3 Bucket, as configured in ALTR.
Data Analysis or Business Intelligence (BI) Tool
The data generated by ALTR is purpose-built to be visualized in a Data Analysis or BI Tool such as PowerBI, Tableau, or Sigma. This is a simple path to a live view of who is accessing data and who is breaching Thresholds.
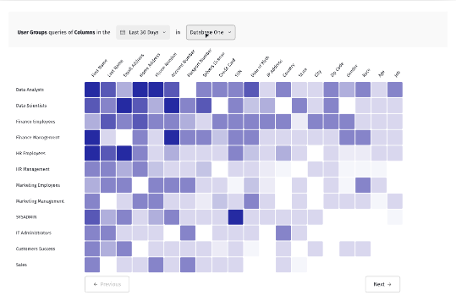
ALTR’s Data Usage Heatmap
ALTR’s natively available Data Usage Heatmap (pictured below) is there for a quick view into what data is being accessed, by what type of users, and at what frequency.
SIEM and SOAR Tools
Using a SIEM or SOAR tool, such as Datadog or Splunk, we can aggregate audits from all systems to fully trace an event and act upon it.
Why Thresholding Matters
Implementing effective thresholds is about more than just compliance—it’s about proactive data security. With ALTR, you can enforce policies that:
- Protect sensitive data without disrupting workflows
- Provide real-time visibility into data activity
- Help you respond quickly and effectively to potential breaches
By setting thresholds tailored to your organization’s unique needs, you ensure that your data is secure, accessible, and used responsibly.
Wrapping Up
Setting effective security thresholds isn’t a one-size-fits-all approach. It requires a combination of robust tools, informed decision-making, and ongoing analysis. With ALTR’s Thresholding feature and real-time insights, you can establish policies that adapt to your organization’s needs, keeping your data secure while enabling your team to operate efficiently.
Take control of your data security today. Start with ALTR and discover how thresholds can transform the way you protect your sensitive information.