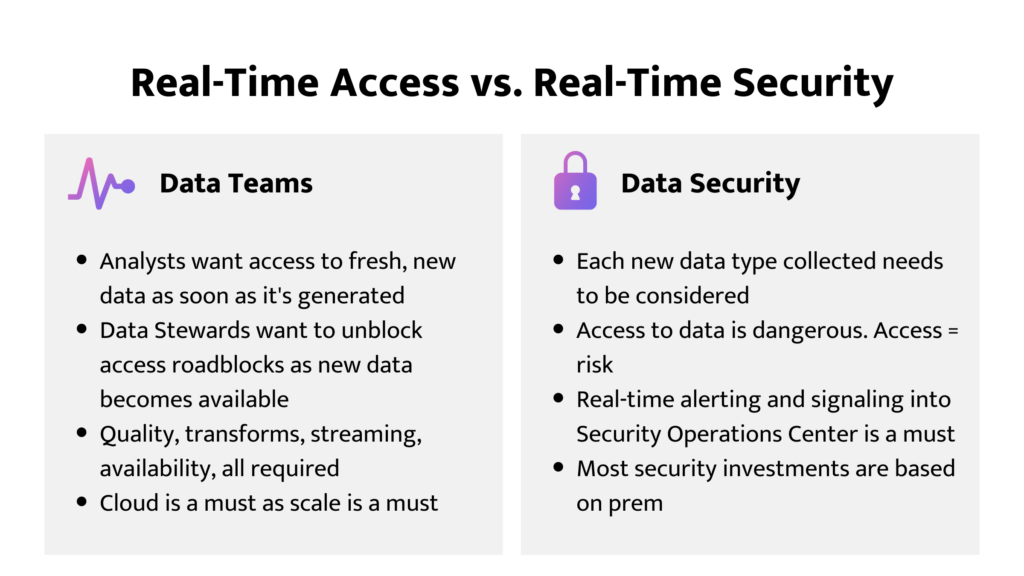
Today’s business environment has no time for silos or lack of collaboration. This challenge is coming to a head at the intersection of data and security. Data teams focus on terms like “quality, accuracy, and availability,” while security teams care about “confidentiality, integrity, and risk reduction.” This often means Data teams want “real-time access” at the same time that Security teams require “real-time security.” But the truth is that both actually have the same goal: extracting maximum business value from the data.
Integrated Security = Streamlined Value
After teams realize they have the same goal, the next step is to converge around shared tools and processes. In many companies, data moves at the speed of the business and increasingly this means at the speed of the cloud. In order to keep up, both data and security teams need tools that have been built for that speed and delivery. The data productivity cloud from Matillion combined with ALTR’s SaaS data access governance and data security platform can be the shared tool set needed to deliver this streamlined value.
Integrated Data Stack
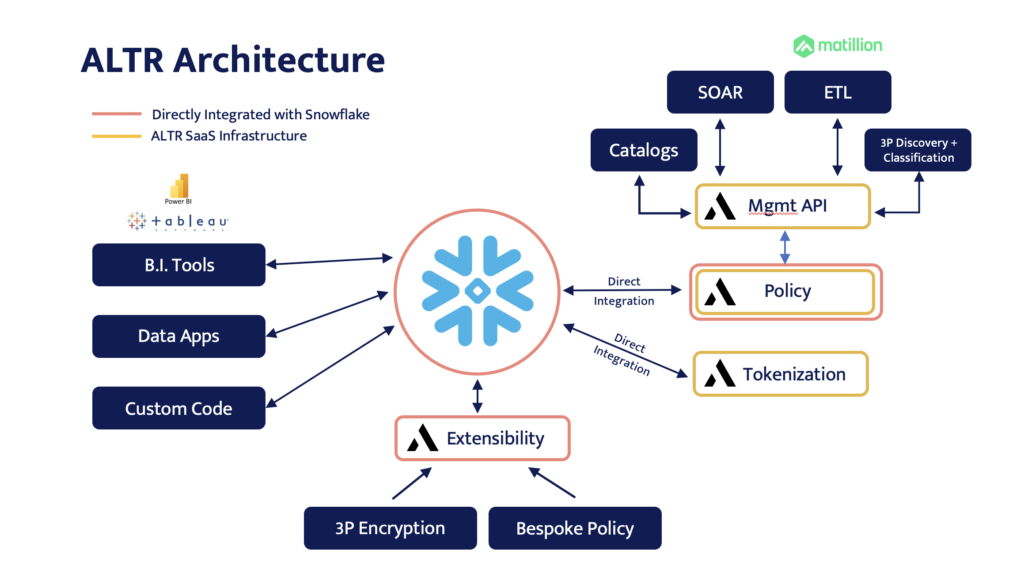
Figure 2 below might look like a complicated data ecosystem, but the point is that it’s actually not. Think about your own stack – this probably looks pretty familiar. That’s because you undoubtedly have a lot going on with the data in your business. What you should notice in this diagram is that Snowflake remains at the center, and everything else works around it. ALTR integrates and works with existing tools to deliver security so that it doesn’t disrupt or interfere with your existing stack – BI tools, Data apps, custom code.
Matillion is a platform to help you get your data business ready faster. It does this by Moving data, Transforming data and Orchestrating the data Pipelines.
ALTR Tokenization + Access Control + Real Time Alerting
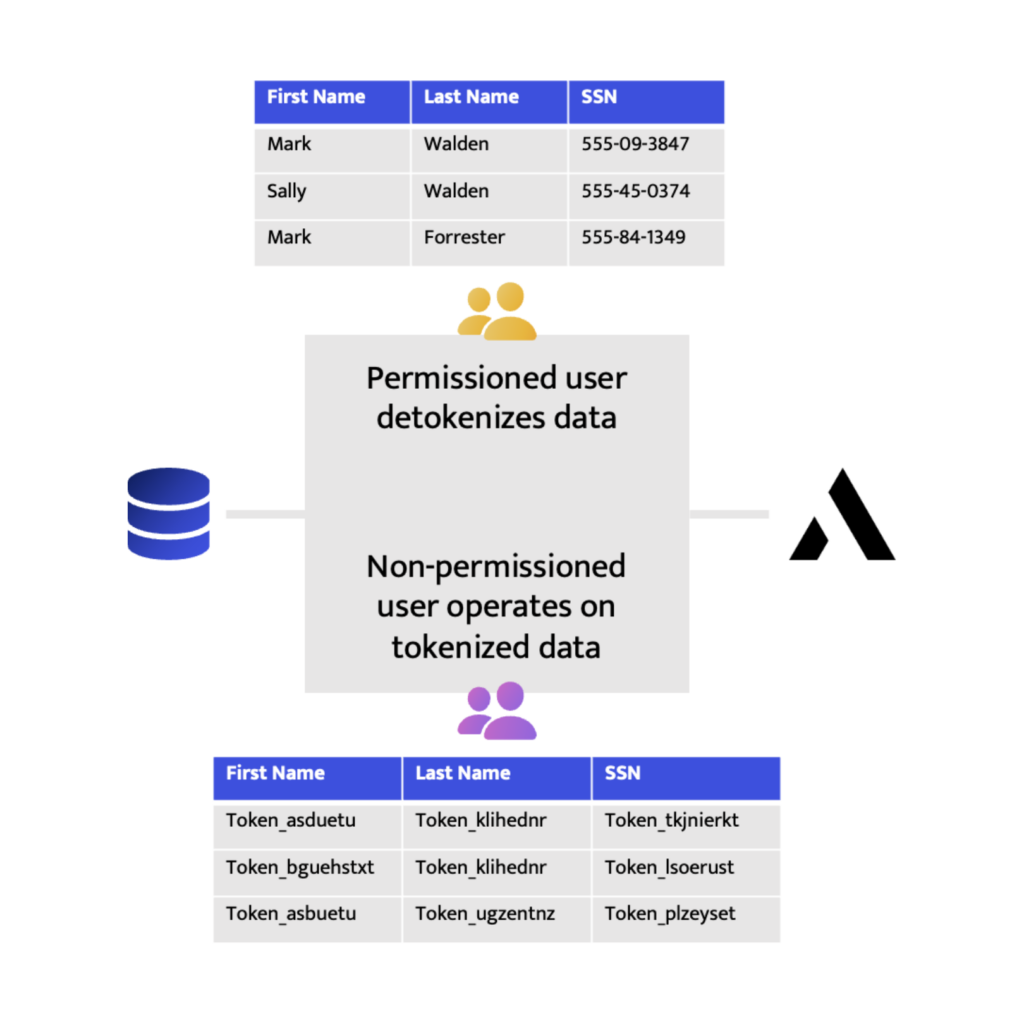
The killer integration to solve for the shared responsibility of CDO and CISO is tokenization + access control + alerting. The ability to ensure privacy, security, and governance are all addressed with a single technology is key. This can be achieved with tokenization plus access control for integrated policy enforcement.
• Data is classified and tagged from ingestion point
• Data is automatically protected at ingestion point based on tag-based policy
• RBAC and other Governance Access items configured once
• Data lands in Snowflake ready to be queried according to policy. No SnowSQL. No SDLC. It just works.
Operationalize Tokenization + Access Control + Real Time Alerting on Matillion Data Productivity Cloud
With ALTR’s new integration for the Matillion Data Productivity cloud, set up is easy – ALTR is natively integrated with Matillion. This native integration is currently a proof-of-concept but will be live on the new Matillion Data Productivity Cloud very soon!
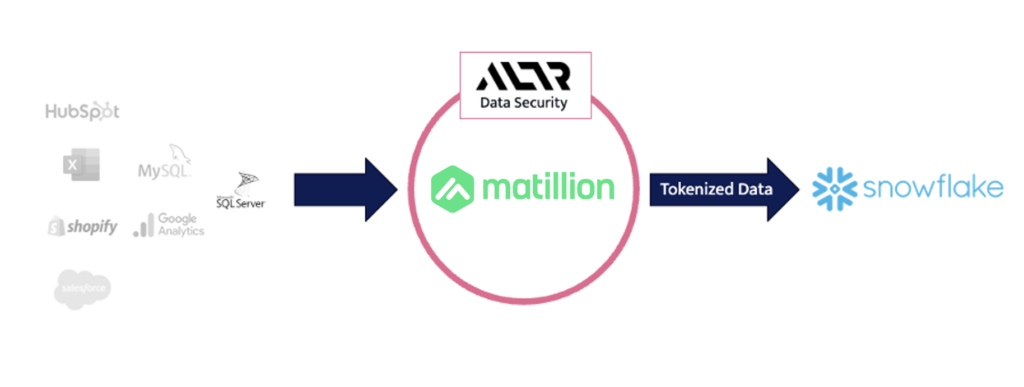
Data classification done by ALTR is set up in Matillion. Then that data is tokenized based on those classification tags automatically when it lands in Snowflake – on the fly. For example, if Social Security numbers are found during the classification process, columns are tagged with SSN, and if the policy requires that data be tokenized, it will be done automatically. This helps to satisfy data security requirements natively in your data pipeline. De-tokenization rules are based on the user, and it doesn’t matter where the user accesses the data from – from Snowflake UI or in Matillion – ALTR’s data access governance policy is applied because data is sitting in Snowflake in its tokenized form. Data teams appreciate this as they want to access the data as soon as it’s available in Snowflake. With tokenization + access control, both teams are getting what they need from the already invested tool sets.
It also doesn’t matter which data source the data originates from – RDS, Workday, SAP, Salesforce. Wherever you’re pulling data from, new data is flowing into the pipeline is categorized, tagged and tokenized based on the pre-set policies around data types. That means whenever data teams want to add another data source, it will be secured.
As this data is accessed, security teams continue to receive customized access history logs which can be configured to alert when certain types of access occur. This access might be outside working hours, across many different data types, or a larger than normal request of sensitive data from a user or a role. Security teams can be certain that only appropriate access is occurring, and data teams know what guardrails they need to operate within.
This solution removes all the bottlenecks of migrating data by doing the hard security stuff required automatically. It also means data teams can stop thinking about security and focus on other data issues like quality and continued migration while knowing they’re meeting the requirements of their partners on the security team.
Full tokenization plus policy integrated directly into your ETL pipeline regardless of the source – no one else makes securing your data migration this easy.


