Format-Preserving Encryption: A Deep Dive into FF3-1 Encryption Algorithm




In the ever-evolving landscape of data security, protecting sensitive information while maintaining its usability is crucial. ALTR’s Format Preserving Encryption (FPE) is an industry disrupting solution designed to address this need. FPE ensures that encrypted data retains the same format as the original plaintext, which is vital for maintaining compatibility with existing systems and applications. This post explores ALTR's FPE, the technical details of the FF3-1 encryption algorithm, and the benefits and challenges associated with using padding in FPE.
Format Preserving Encryption is a cryptographic technique that encrypts data while preserving its original format. This means that if the plaintext data is a 16-digit credit card number, the ciphertext will also be a 16-digit number. This property is essential for systems where data format consistency is critical, such as databases, legacy applications, and regulatory compliance scenarios.
The FF3-1 encryption algorithm is a format-preserving encryption method that follows the guidelines established by the National Institute of Standards and Technology (NIST). It is part of the NIST Special Publication 800-38G and is a variant of the Feistel network, which is widely used in various cryptographic applications. Here’s a technical breakdown of how FF3-1 works:
1. Feistel Network: FF3-1 is based on a Feistel network, a symmetric structure used in many block cipher designs. A Feistel network divides the plaintext into two halves and processes them through multiple rounds of encryption, using a subkey derived from the main key in each round.
2. Rounds: FF3-1 typically uses 8 rounds of encryption, where each round applies a round function to one half of the data and then combines it with the other half using an XOR operation. This process is repeated, alternating between the halves.
3. Key Scheduling: FF3-1 uses a key scheduling algorithm to generate a series of subkeys from the main encryption key. These subkeys are used in each round of the Feistel network to ensure security.
4. Tweakable Block Cipher: FF3-1 includes a tweakable block cipher mechanism, where a tweak (an additional input parameter) is used along with the key to add an extra layer of security. This makes it resistant to certain types of cryptographic attacks.
5. Format Preservation: The algorithm ensures that the ciphertext retains the same format as the plaintext. For example, if the input is a numeric string like a phone number, the output will also be a numeric string of the same length, also appearing like a phone number.
1. Initialization: The plaintext is divided into two halves, and an initial tweak is applied. The tweak is often derived from additional data, such as the position of the data within a larger dataset, to ensure uniqueness.
2. Round Function: In each round, the round function takes one half of the data and a subkey as inputs. The round function typically includes modular addition, bitwise operations, and table lookups to produce a pseudorandom output.
3. Combining Halves: The output of the round function is XORed with the other half of the data. The halves are then swapped, and the process repeats for the specified number of rounds.
4. Finalization: After the final round, the halves are recombined to form the final ciphertext, which maintains the same format as the original plaintext.
Implementing FPE provides numerous benefits to organizations:
1. Compatibility with Existing Systems: Since FPE maintains the original data format, it can be integrated into existing systems without requiring significant changes. This reduces the risk of errors and system disruptions.
2. Improved Performance: FPE algorithms like FF3-1 are designed to be efficient, ensuring minimal impact on system performance. This is crucial for applications where speed and responsiveness are critical.
3. Simplified Data Migration: FPE allows for the secure migration of data between systems while preserving its format, simplifying the process and ensuring compatibility and functionality.
4. Enhanced Data Security: By encrypting sensitive data, FPE protects it from unauthorized access, reducing the risk of data breaches and ensuring compliance with data protection regulations.
5. Creation of production-like data for lower trust environments: Using a product like ALTR’s FPE, data engineers can use the cipher-text of production data to create useful mock datasets for consumption by developers in lower-trust development and test environments.
Padding is a technique used in encryption to ensure that the plaintext data meets the required minimum length for the encryption algorithm. While padding is beneficial in maintaining data structure, it presents both advantages and challenges in the context of FPE:
1. Consistency in Data Length: Padding ensures that the data conforms to the required minimum length, which is necessary for the encryption algorithm to function correctly.
2. Preservation of Data Format: Padding helps maintain the original data format, which is crucial for systems that rely on specific data structures.
3. Enhanced Security: By adding extra data, padding can make it more difficult for attackers to infer information about the original data from the ciphertext.
1. Increased Complexity: The use of padding adds complexity to the encryption and decryption processes, which can increase the risk of implementation errors.
2. Potential Information Leakage: If not implemented correctly, padding schemes can potentially leak information about the original data, compromising security.
3. Handling of Padding in Decryption: Ensuring that the padding is correctly handled during decryption is crucial to avoid errors and data corruption.
ALTR's Format Preserving Encryption, powered by the technically robust FF3-1 algorithm and married with legendary ALTR policy, offers a comprehensive solution for encrypting sensitive data while maintaining its usability and format. This approach ensures compatibility with existing systems, enhances data security, and supports regulatory compliance. However, the use of padding in FPE, while beneficial in preserving data structure, introduces additional complexity and potential security challenges that must be carefully managed. By leveraging ALTR’s FPE, organizations can effectively protect their sensitive data without sacrificing functionality or performance.
For more information about ALTR’s Format Preserving Encryption and other data security solutions, visit the ALTR documentation

For years (even decades) sensitive information has lived in transactional and analytical databases in the data center. Firewalls, VPNs, Database Activity Monitors, Encryption solutions, Access Control solutions, Privileged Access Management and Data Loss Prevention tools were all purchased and assembled to sit in front of, and around, the databases housing this sensitive information.
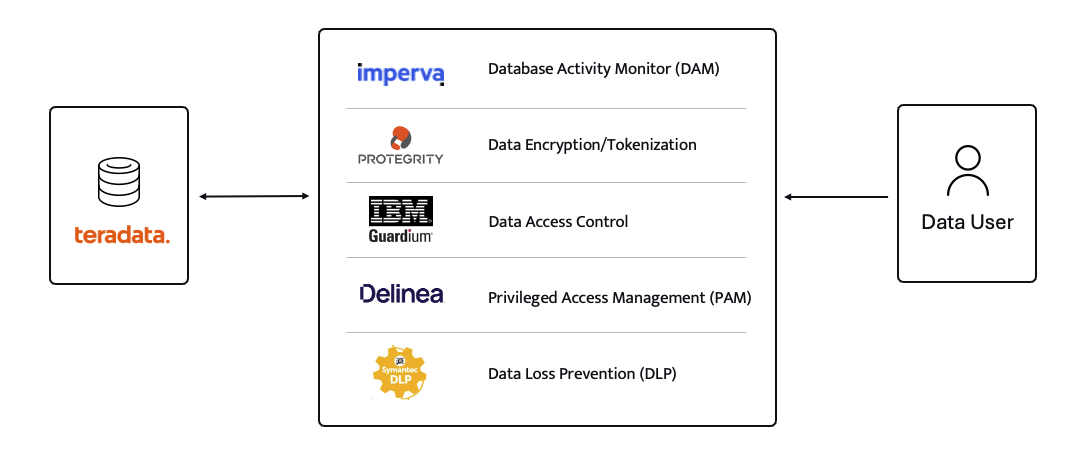
Even with all of the above solutions in place, CISO’s and security teams were still a nervous wreck. The goal of delivering data to the business was met, but that does not mean the teams were happy with their solutions. But we got by.
The advent of Big Data and now Generative AI are causing businesses to come to terms with the limitations of these on-prem analytical data stores. It’s hard to scale these systems when the compute and storage are tightly coupled. Sharing data with trusted parties outside the walls of the data center securely is clunky at best, downright dangerous in most cases. And forget running your own GenAI models in your datacenter unless you can outbid Larry, Sam, Satya, and Elon at the Nvidia store. These limits have brought on the era of cloud data platforms. These cloud platforms address the business needs and operational challenges, but they also present whole new security and compliance challenges.
ALTR’s platform has been purpose-built to recreate and enhance these protections required to use Teradata for Snowflake. Our cutting-edge SaaS architecture is revolutionizing data migrations from Teradata to Snowflake, making it seamless for organizations of all sizes, across industries, to unlock the full potential of their data.
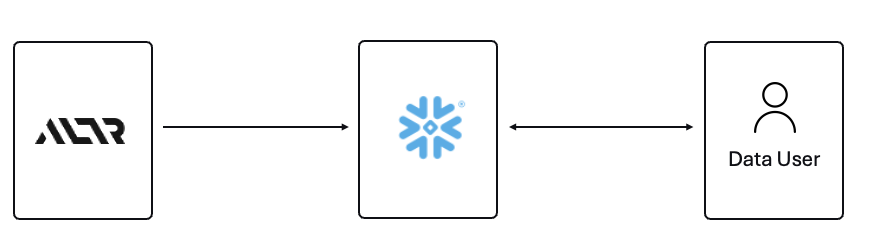
What spurred this blog is that a company reached out to ALTR to help them with data security on Snowflake. Cool! A member of the Data & Analytics team who tried our product and found love at first sight. The features were exactly what was needed to control access to sensitive data. Our Format-Preserving Encryption sets the standard for securing data at rest, offering unmatched protection with pricing that's accessible for businesses of any size. Win-win, which is the way it should be.
Our team collaborated closely with this person on use cases, identifying time and cost savings, and mapping out a plan to prove the solution’s value to their organization. Typically, we engage with the CISO at this stage, and those conversations are highly successful. However, this was not the case this time. The CISO did not want to meet with our team and practically stalled our progress.
The CISO’s point of view was that ALTR’s security solution could be completely disabled, removed, and would not be helpful in the case of a compromised ACCOUNTADMIN account in Snowflake. I agree with the CISO, all of those things are possible. Here is what I wanted to say to the CISO if they had given me the chance to meet with them!
The ACCOUNTADMIN role has a very simple definition, yet powerful and long-reaching implications of its use:

One of the main points I would have liked to make to the CISO is that as a user of Snowflake, their responsibility to secure that ACCOUNTADMIN role is squarely in their court. By now I’m sure you have all seen the news and responses to the Snowflake compromised accounts that happened earlier this year. It is proven that unsecured accounts by Snowflake customers caused the data theft. There have been dozens of articles and recommendations on how to secure your accounts with Snowflake and even a mandate of minimum authentication standards going forward for Snowflake accounts. You can read more information here, around securing the ACCOUNTADMIN role in Snowflake.
I felt the CISO was missing the point of the ALTR solution, and I wanted the chance to explain my perspective.
ALTR is not meant to secure the ACCOUNTADMIN account in Snowflake. That’s not where the real risk lies when using Snowflake (and yes, I know—“tell that to Ticketmaster.” Well, I did. Check out my write-up on how ALTR could have mitigated or even reduced the data theft, even with compromised accounts). The risk to data in Snowflake comes from all the OTHER accounts that are created and given access to data.
The ACCOUNTADMIN role is limited to one or two people in an organization. These are trusted folks who are smart and don’t want to get in trouble (99% of the time). On the other hand, you will have potentially thousands of non-ACCOUNTADMIN users accessing data, sharing data, screensharing dashboards, re-using passwords, etc. This is the purpose of ALTR’s Data Security Platform, to help you get a handle on part of the problem which is so large it can cause companies to abandon the benefits of Snowflake entirely.
There are three major issues outside of the ACCOUNTADMIN role that companies have to address when using Snowflake:
1. You must understand where your sensitive is inside of Snowflake. Data changes rapidly. You must keep up.
2. You must be able to prove to the business that you have a least privileged access mechanism. Data is accessed only when there is a valid business purpose.
3. You must be able to protect data at rest and in motion within Snowflake. This means cell level encryption using a BYOK approach, near-real-time data activity monitoring, and data theft prevention in the form of DLP.
The three issues mentioned above are incredibly difficult for 95% of businesses to solve, largely due to the sheer scale and complexity of these challenges. Terabytes of data and growing daily, more users with more applications, trusted third parties who want to collaborate with your data. All of this leads to an unmanageable set of internal processes that slow down the business and provide risk.
ALTR’s easy-to-use solution allows Virgin Pulse Data, Reporting, and Analytics teams to automatically apply data masking to thousands of tagged columns across multiple Snowflake databases. We’re able to store PII/PHI data securely and privately with a complete audit trail. Our internal users gain insight from this masked data and change lives for good.
- Andrew Bartley, Director of Data Governance
I believed the CISO at this company was either too focused on the ACCOUNTADMIN problem to understand their other risks, or felt he had control over the other non-admin accounts. In either case I would have liked to learn more!
There was a reason someone from the Data & Analytics team sought out a product like ALTR. Data teams are afraid of screwing up. People are scared to store and use sensitive data in Snowflake. That is what ALTR solves for, not the task of ACCOUNTADMIN security. I wanted to be able to walk the CISO through the risks and how others have solved for them using ALTR.
The tools that Snowflake provides to secure and lock down the ACCOUNTADMIN role are robust and simple to use. Ensure network policies are in place. Ensure MFA is enabled. Ensure you have logging of ACCOUNTADMIN activity to watch all access.
I wish I could have been on the conversation with the CISO to ask a simple question, “If I show you how to control the ACCOUNTADMIN role on your own, would that change your tone on your teams use of ALTR?” I don’t know the answer they would have given, but I know the answer most CISO’s would give.
Nothing will ever be 100% secure and I am by no means saying ALTR can protect your Snowflake data 100% by using our platform. Data security is all about reducing risk. Control the things you can, monitor closely and respond to the things you cannot control. That is what ALTR provides day in and day out to our customers. You can control your ACCOUNTADMIN on your own. Let us control and monitor the things you cannot do on your own.

Since 2015 the migration of corporate data to the cloud has rapidly accelerated. At the time it was estimated that 30% of the corporate data was in the cloud compared to 2022 where it doubled to 60% in a mere seven years. Here we are in 2024, and this trend has not slowed down.
Over time, as more and more data has moved to the cloud, new challenges have presented themselves to organizations. New vendor onboarding, spend analysis, and new units of measure for billing. This brought on different cloud computer-related cost structures and new skillsets with new job titles. Vendor lock-in, skill gaps, performance and latency and data governance all became more intricate paired with the move to the cloud. Both operational and transactional data were in scope to reap the benefits promised by cloud computing, organizational cost savings, data analytics and, of course, AI.
The most critical of these new challenges revolve around a focus on Data Security and Privacy. The migration of on-premises data workloads to the Cloud Data Warehouses included sensitive, confidential, and personal information. Corporations like Microsoft, Google, Meta, Apple, Amazon were capturing every movement, purchase, keystroke, conversation and what feels like thought we ever made. These same cloud service providers made this easier for their enterprise customers to do the same. Along came Big Data and the need for it to be cataloged, analyzed, and used with the promise of making our personal lives better for a cost. The world's population readily sacrificed privacy for convenience.
The moral and ethical conversation would then begin, and world governments responded with regulations such as GDPR, CCPA and now most recently the European Union’s AI Act. The risk and fines have been in the billions. This is a story we already know well. Thus, Data Security and Privacy have become a critical function primarily for the obvious use case, compliance, and regulation. Yet only 11% of organizations have encrypted over 80% of their sensitive data.
With new challenges also came new capabilities and business opportunities. Real time analytics across distributed data sources (IoT, social media, transactional systems) enabling real time supply chain visibility, dynamic changes to pricing strategies, and enabling organizations to launch products to market faster than ever. On premise applications could not handle the volume of data that exists in today’s economy.
Data sharing between partners and customers became a strategic capability. Without having to copy or move data, organizations were enabled to build data monetization strategies leading to new business models. Now building and training Machine Learning models on demand is faster and easier than ever before.
To reap the benefits of the new data world, while remaining compliant, effective organizations have been prioritizing Data Security as a business enabler. Format Preserving Encryption (FPE) has become an accepted encryption option to enforce security and privacy policies. It is increasingly popular as it can address many of the challenges of the cloud while enabling new business capabilities. Let’s look at a few examples now:
Real Time Analytics - Because FPE is an encryption method that returns data in the original format, the data remains useful in the same length, structure, so that more data engineers, scientists and analysts can work with the data without being exposed to sensitive information.
Data Sharing – FPE enables data sharing of sensitive information both personal and confidential, enabling secure information, collaboration, and innovation alike.
Proactive Data Security– FPE allows for the anonymization of sensitive information, proactively protecting against data breaches and bad actors. Good holding to ransom a company that takes a more proactive approach using FPE and other Data Security Platform features in combination.
Empowered Data Engineering – with FPE data engineers can still build, test and deploy data transformations as user defined functions and logic in stored procedures or complied code will run without failure. Data validations and data quality checks for formats, lengths and more can be written and tested without exposing sensitive information. Federated, aggregation and range queries can still run without fail without the need for decryption. Dynamic ABAC and RBAC controls can be combined to decrypt at runtime for users with proper rights to see the original values of data.
Cost Management – While FPE does not come close to solving Cost Management in its entirety, it can definitely contribute. We are seeing a need for FPE as an option instead of replicating data in the cloud to development, test, and production support environments. With data transfer, storage and compute costs, moving data across regions and environments can be really expensive. With FPE, data can be encrypted and decrypted with compute that is a less expensive option than organizations' current antiquated data replication jobs. Thus, making FPE a viable cost savings option for producing production ready data in non-production environments. Look for a future blog on this topic and all the benefits that come along.
FPE is not a silver bullet for protecting sensitive information or enabled these business use cases. There are well documented challenges in the FF1 and FF3-1 algorithms (another blog on that to come). A blend of features including data discovery, dynamic data masking, tokenization, role and attribute-based access controls and data activity monitoring will be needed to have a proactive approach towards security within your modern data stack. This is why Gartner considers a Data Security Platform, like ALTR, to be one of the most advanced and proactive solutions for Data security leaders in your industry.
Securing sensitive information is now more critical than ever for all types of organizations as there have been many high-profile data breaches recently. There are several ways to secure the data including restricting access, masking, encrypting or tokenization. These can pose some challenges when using the data downstream. This is where Format Preserving Encryption (FPE) helps.
This blog will cover what Format Preserving Encryption is, how it works and where it is useful.
Whereas traditional encryption methods generate ciphertext that doesn't look like the original data, Format Preserving Encryption (FPE) encrypts data whilst maintaining the original data format. Changing the format can be an issue for systems or humans that expect data in a specific format. Let's look at an example of encrypting a 16-digit credit card number:

As you can see with a Standard Encryption type the result is a completely different output. This may result in it being incompatible with systems which require or expect a 16-digit numerical format. Using FPE the encrypted data still looks like a valid 16-digit number. This is extremely useful for where data must stay in a specific format for compatibility, compliance, or usability reasons.
Format Preserving Encryption in ALTR works by first analyzing the column to understand the input format and length. Next the NIST algorithm is applied to encrypt the data with the given key and tweak. ALTR applies regular key rotation to maximize security. We also support customers bringing their own keys (BYOK). Data can then selectively be decrypted using ALTR’s access policies.
FPE offers several benefits for organizations that deal with structured data:
1. Adds extra layer of protection: Even if a system or database is breached the encryption makes sensitive data harder to access.
2. Original Data Format Maintained: FPE preserves the original data structure. This is critical when the data format cannot be changed due to system limitations or compliance regulations.
3. Improves Usability: Encrypted data in an expected format is easier to use, display and transform.
4. Simplifies Compliance: Many regulations like PCI-DSS, HIPAA, and GDPR will mandate safeguarding, such as encryption, of sensitive data. FPE allows you to apply encryption without disrupting data flows or reporting, all while still meeting regulatory requirements.
FPE is widely adopted in industries that regularly handle sensitive data. Here are a few common use cases:
ALTR offers various masking, tokenization and encryption options to keep all your Snowflake data secure. Our customers are seeing the benefit of Format Preserving Encryption to enhance their data protection efforts while maintaining operational efficiency and compliance. For more information, schedule a product tour or visit the Snowflake Marketplace.

After another up and down year of COVID, I’m looking forward to some holiday joy, and to some fun holiday shopping. Like many others since the start of the pandemic I’ll be doing a lot of that buying from home, online. And some of the hottest items on the list – from smart watches to picture frames – come with internet connectivity built in. All of this has me wondering about the data that will be collected about me or my family in the upcoming holiday season.
Many of the articles I found when searching for “online holiday shopping data privacy” put the responsibility on consumers, with reems of advice on what we should do to protect our data. But that’s actually harder for consumers than ever. Although a handful of state-level privacy regulations were passed this year, the lack of a consistent state by state consumer data privacy laws, or a US federal law like GDPR, makes it very challenging for consumers to understand what they’re agreeing to or what they might be giving up.
This means online retailers must step up. The flip side to the benefits of gathering data is the responsibility to keep it safe. Is your data privacy program ready for the holiday season? Is it naughty or nice?
COVID-19 threw a hitch into a lot of normal activities last year – from working from home to learning from home to watching movies from home. Sensing a trend? Holiday shopping was no exception. Before last year’s shopping season, a Deliotte survey showed 64% of respondents planned to spend their holiday shopping budgets online. For the first time, Cyber Monday surpassed Black Friday with 59% of respondents planning to shop on Cyber Monday versus 48% on Black Friday.

The trend continues this year with two-thirds (66%) of respondents to a leading customer data platform survey saying they buy online now more than they did before the pandemic. For the holidays this year, nearly half plan to combine in-store and online shopping, and more than one-third plan to use e-commerce exclusively.
This increase in online shopping has led to an increase in online shopping data – creating both a windfall and a responsibility for retailers.
COVID has convinced some consumers to overcome their distrust of online shopping – the Holiday Shopping ID Theft survey showed that 73% of those who avoided online shopping in the past say they have become more comfortable shopping online since the start of the pandemic. But 66% of surveyed still expressed concern about their financial or personal information being compromised due to a data breach while shopping this holiday season.

This concern is no surprise – even though most consumers are unaware of all the data gathered about them while online shopping, even just the leak of name, a credit card number, and address could lead to issues. On top of that, retailers collect info about what customers are buying, sites visited, products considered, browsing patterns, and more. Consumers say they value privacy over customized marketing, but as customized marketing continues to be effective for retailers, there are no signs of this slowing.
It’s practically impossible for consumers to have a clear idea of all the data companies are gathering on them because it’s primarily behind the scenes, with a cookie notification popping up here and there. And let’s be honest, we all just click whatever it takes to make the pop up go away and get on with our shopping – just like we do with terms and conditions! Companies that value their customer relationships should take these steps to keep customer data as secure as this year’s secret Santa list:
With so much being thrown at consumers over the last two years, the best gift retailers can give their customers this holiday season is to take one more worry off their plates: data privacy. Retailers need to ensure sensitive and private customer data is controlled and protected, keeping it safe, so consumers can just focus on finding the latest, coolest gadgets and spreading holiday cheer in a year when we need that more than ever.


When you analyze a company’s journey as it becomes a more data-driven organization, you start to see some pretty clear patterns. Invariably, we see customers walking the path below regardless of industry vertical or company size:
Everyone has these same needs around their sensitive data—and a heck of a lot more—but these are what we keep seeing as core requirements. The very first item on this path is sensitive data classification. If you think about it, you can’t really get started until you understand what and where your sensitive data is. Once you do that, applying governance and security policies is a matter of doing the work (for any data engineers reading, yes, a lot of work. Contact us!)
Learn about what is considered sensitive data and what kind of security it requires.
Heck, we need sensitive data classification too. It allows us to better understand and report on data consumption, more easily apply access governance controls, detect sensitive data in new data sources, and help our customers be confident that their data is both private and secure.
When it comes to sensitive data classification, there are products out there doing a great job at that already. To add support in our own platform, we didn’t need to reinvent the wheel, we just had to add the classification “wheel” to our product’s “car”. Our customers can simply choose which classification provider they use, and ALTR’s integrations will take care of the rest, improving reporting on data access and making it even easier to implement governance controls.
For companies without a current classification provider, we have out-of-the-box integrations for Google DLP and Snowflake's native classification so everyone who uses ALTR can start on the path to full data access governance and security easily.

At ALTR, we want remove the burdens of data classification as you grow, add more data, users, and platforms into the mix. We do as much of the heavy lifting ourselves as possible, delivering new and unique features that layer advanced data security on top of governance controls (for a primer on how governance and security are intertwined, check out this blog post. But we also believe this involves connecting the broader data ecosystem together so the tools and platforms you use share a unified understanding of your data. We’re excited that our support for data classification is an extension of this belief.

The 2020 Verizon Breach Report shows that breaches are up nearly 100% from last year, and threats are evolving at an alarming rate with more and more people working from home since March of 2020. This marks the fourth year in a row that stolen credentials are the number one source of breaches and hacking. (For our purposes here, hackers can be defined, at a very high level, as one of three things: those utilizing stolen or brute-forced credentials; those exploiting vulnerabilities; attackers using backdoors and command and control [C2] functionality.) Four years in a row is certainly long enough to call it an established trend, so let’s talk about why this is happening.
To start, we’ll explore the vectors where attacks are happening less. Websites are getting smarter about SSL/TLS, so plain text interception attacks are on the decline. Browsers like Google Chrome and Firefox are getting more aggressive about protecting against man-in-the-middle and eavesdropping attacks, leading to a decrease in IP spoofing, SSL hijacking, and the like. While it’s great news that these types of attacks are trending downward, the consequence is that now the only way in is with usernames and passwords. That’s great news for attackers since most people are lazy when it comes to their passwords... but bad news for users.
Do you use one key for your house, storage unit, office, safe, bike lock, and car? Probably not. It should really be no different when it comes to your different online services; if you use one password or a variation of one password for your Netflix, email, bank account, E*Trade, etc., then guess what? If someone steals your password, they’re going to have a field day with all that data. Maybe you’re not the type of person who uses a similar password for everything... but the average person certainly does. A recent blog published by eBanking platform Q2 shows that most people have more than 200 online accounts and only 8-10 unique passwords. So if I guess or steal one of your passwords, that means I’ll have access to at least 20 of your accounts (on average, of course).
Obviously it would be a huge pain to have to create a complex, really-hard-to-guess, unique password for each of your ~200 accounts. Wouldn’t it be great if there was a tool that could do that for you? Aha! There is. It’s called a password manager, and you should 100% use one. You can’t really go wrong when picking one: there’s LastPass, OneLogin, KeePass, Dashlane, and plenty more. Even your web browsers like Chrome, Firefox, and Safari have native password management capabilities (though we’d warn against those as most of them store your passwords on your computer in an unencrypted form).
Either way, any password manager is better than using the same password for all accounts. Use one for your personal accounts; use one for your work accounts; use one for everything! Just use it, please.
Even as a security expert, I didn’t realize how important a password manager was until a few years ago. I used to have three passwords: one without numbers, one with numbers, and one with numbers and symbols. The end. But then I got smarter, and I started using LastPass – I’m safer; my company is safer; my family is safer; and everything is just oh-so-much better (and easier). If you don’t believe me, maybe you'll listen to Forrester Analyst, Brian Kime, who claims that a password manager “could save your marriage”... just saying.
It’s not hard to start using either, and it doesn't have to be a whole big event. Download the password manager and as you go about your normal day logging into sites or services, just spend 30 seconds max changing your password for each site you visit. That’s all there is to it!
And if you’re wondering, “what if someone steals the password for my password manager?!” Well, I’d recommend using a device where you can use your fingerprint or face scan to login; in lieu of that, a password manager will also generate a random, nearly impossible-to-guess password for you. So just do it.
The cybersecurity journey is never over since bad actors are constantly evolving along with new technologies. Password managers are just the first step to protecting your sensitive data. But as we mentioned at the beginning, stolen passwords are still on the rise. So, along with password managers, organizations need a strategy to ensure their data is safe if/when credentials are compromised. That’s where ALTR can help.

Whether at work or for personal purposes, it seems like every website from online stores to news outlets requires a login these days. That’s a lot of passwords for you to manage, and it’s only human to take a shortcut or two. But even when you follow every password best practice, hackers have a way of getting around your defenses. According to a recent Verizon report, 81% of data breaches involve weak or stolen passwords. With employees who have passwords for countless applications, how can organizations possibly keep their data safe day in and day out? You need to understand the threat before you can find the solution that best fits your situation. In part one of this series we will explore the threats around guessed and stolen credentials.
Humans are creatures of habit, and hackers are very aware of it. By using brute force or dictionary attacks – or simply by peering over someone’s shoulder – hackers essentially “guess” user passwords based on their knowledge of password habits and open source intelligence. This is especially true for weak passwords (“123456,” “111111” and “password,” to name a few) that continue to be frequently used across multiple applications and platforms. To quote a prophetic 1970s Jackson 5 lyric, “abc, it’s as easy as 123.”
Passwords are like stocks; you should never put all of your faith in just one. No matter how strong and reliable a password seems, it only takes one high-profile data breach (Target, Capital One, Equifax, etc.) to land a clever arrangement of numbers, letters and punctuation marks on some international hacker database. In a survey of 1000 individuals in the US, more than half used the same password for multiple online logins. When employees use the same password for everything, including your website or app, it’s like they’re handing cybercriminals a key to your front door.
Even when someone gets that dreaded notification that one of their (hopefully many) passwords has been compromised, they’ll often “wait it out” or change a single character instead of coming up with something completely different. Cybersecurity expert Troy Hunt notes that once a password or passphrase is exposed by a data breach, it is no longer secure. Attackers hoard the information exposed in these breaches and engage in credential stuffing, testing the combinations on unrelated sites. It’s only a matter of time before they discover your employee couldn’t be bothered to significantly change their credentials.
Cybercriminals are also adept at manipulating credentialed users into giving away passwords through phishing and spear-phishing campaigns. Take the “rescheduled meeting” scam popping up in thousands of corporate inboxes earlier this year, where employees were duped into providing hackers with their usernames and passwords. One study shows that even after implementing security awareness and phishing identification training programs in a workplace, users click on phishing emails almost 25% of the time. Encouraging your employees to keep a close eye on their inboxes could stop you from becoming some hacker’s greatest catch.
So how should organizations prevent a cybercriminal from getting to their sensitive data through employees’ passwords? While all of the steps above are helpful to preventing stolen passwords, the bottom line is you need to still assume someone will get through. You need to have technology and policy in place to protect your data even when a cybercriminal gets access to credentials. ALTR’s Data Security platform allows you to mask certain data so that the employee only has access to the fewest fields that they need in order to do their job. This means the cybercriminal only has access to minimal fields if/when they get into the application. Secondly, ALTR allows you to set thresholds for how much data an employee can access. When the cybercriminal or disgruntled employee tries to smash and grab all the data, they will only get away with a fragment of the data they were trying to get. These innovative security measures make compromised credentials a concern of the past.

Even in the best of times, it can be a lonely experience living away from family in a retirement home or extended-living facility. But during the current coronavirus epidemic, residents of these homes are more isolated than usual, and often completely shut in. In this setting, something as simple as having a smartphone for video calls with family members can make a real difference in residents’ quality of life.
Working in tech, we at ALTR often use the latest models of smartphones for work and personal tasks. When we recently found ourselves with a surplus of slightly older phones that still had plenty of life in them, we looked for a way to repurpose the phones in the Austin area, where ALTR is headquartered. The opportunity we found exceeded our expectations.
Working with a local contact, we first determined the need for phones in local nursing homes. Then, ALTR’s technical crew made sure the phones were securely erased of any sensitive data and matched with the appropriate plugs and cables. Then we delivered them to the homes that needed them most.
Because each home typically has just one shared house phone without video, having a good smartphone or two on hand is a big plus for enabling residents to see their loved ones’ faces as they talk with them. Over the past couple of weeks, our team has distributed 20 phones to more than a dozen nursing and extended-living homes in Austin and nearby towns.
The staff at one assisted-living facility reported that they have now explained to their clients how family members of residents can take advantage of the new opportunity to connect. They assured us that the phone “is very much appreciated and definitely will be used.”
We know that this is just a small effort in these trying times, but we were happy we could take these steps to meet a real need for people in our community. And we’ll keep looking for new ways to help.
If you’d like to do the same, search for organizations in your area that are collecting donations in response to COVID-19. Here in Austin, for instance, the Ascension Texas healthcare group has guidelines for donating used iPads, along with new medical supplies such as personal protective equipment (PPE). Meanwhile, the national non-profit #CareNotCOVIDinitiative can help you find local facilities for giving nursing homes new electronic devices, books, games, medical supplies, and more. We hope you’ll consider pitching in!

Imagine this scenario: you’re a CISO for a multi-billion-dollar retailer or manufacturer. Data has become critical to how your business is run. So much so that you have one thousand-plus users accessing data from Snowflake, and you have a data analysis team of 40. Early one morning an analyst appears to run a query that would return more than 7 million rows of PII data.
What happens next? Does he get the data, or do you stop him?
It all depends on the choices you’ve made up to that point…
Before you get to this juncture, there are a few critical steps you can take to ensure you have the right information and options available to you.
1. Everything starts with Observability – ALTR’s integration with Snowflake provides complete observability over any sensitive data you tell ALTR to watch. This ensures that every request for, and usage of, this data is recorded and available to you as soon as it’s added to ALTR.
2. Next comes data consumption patterns - The next step is patterning data consumption so you can begin to understand what normal consumption looks like. The easiest way to do this is by setting up a scaled set of “alert and log” signals in ALTR, which can be streamed to your Snowflake Security Data Lake. This will allow you to group access records by tiered amounts and give you additional context into which roles and users access what types of data and in what quantities. A sample tier of Alerts could include logging any users and/or roles which request:
3. Seeing what "normal" looks like - After just a week, data usage alerts in your SIEM or in your Snowflake Security Data Lake can easily be visualized into a curve that represents your normal data consumption pattern. For example, the details below demonstrate that 99.5% of data consumption is made through requests for 10,000 or fewer records, while 81.4% occurred through requests for 1,000 records or less.
4. Reducing the risk - Understanding how various users and roles across the business consume data to perform their functions allows you to optimize your access, alerting and blocking polices based on normal and necessary usage. You can set consumption polices just outside of what your alert patterns show you represents normal consumption and, over time, you can refine these consumption limits on an ongoing basis to continually the reduce risk posed by credentialed access threats.
Let’s go back to our CISO and the analyst’s early morning access request. With ALTR and Snowflake Security Data Lake in place, the CISO will receive a real-time alert triggering a blocked access for the specific analyst (with no other analyst or data users affected). The CISO asks his team to take a look at the security data lake to investigate. They find that over the past 120 days:
99.7% of all queries run by any role on the analyst team returned 100,000 rows or less
68.4% of queries returned 10,000 rows or less
32.6% returned 1,000 or less
12.7% returned 100 or less
For Analyst II role (this user), the largest query to date returned 1.2 million records
Since his hire, this analyst has averaged 18,788 PII records a day
Daily and hourly details of PII consumption for every user and role:
With this historical visibility available, it’s obvious this request is completely abnormal. The CISO calls the Director of the analysis team to inform her that the analyst is blocked and that a security event is being investigated. The Director lets the CISO know that this particular analyst is on PTO today. The CISO can then take the step of de-authorizing the analyst’s access to all systems enterprise-wide due to the threat that his credentials have been compromised. A security incident is created, and an investigation is launched.
Credentialed access threats continue to be one of the top drivers of sensitive data breaches according to both the Verizon Data Breach Investigation Report and the IBM Cost of a Data Breach Report. They’re possible to stop, but it’s not as simple as turning on a firewall. It requires preparation and diligence to get ahead of the risk, to first understand what normal data consumption looks like so you can quickly spot abnormal access.
It’s up to you: would you rather be prepared or caught flat footed? Your choice will determine what happens when a credentialed access threat crosses your path.


Congratulations on kicking off your Snowflake journey! Or at least thinking about starting your journey with Snowflake. This puts you among the thousands of companies working with Snowflake to extract the maximum value from their data. And, based on what we’ve seen so far, I feel pretty confident that your Snowflake project will be successful. Before you know it, you’ll be inundated with requests – your colleagues will want more and more and more – and they’ll all want the answer yesterday. You’ll go from two users to 10 to 1,000 with no time to catch a breath.
To ensure you’re keeping up with the speed of your business and not lagging behind from day one, it’s critical to have the right tools for your journey from the very start. That means including a data governance and security solution. This may not be on your list of priorities today – maybe you’re focused on other tasks, don’t think you need it, or believe it’s too time-consuming, complicated or costly.
But you won’t be able to get the most value from your Snowflake project as quickly if you don’t have an effective data governance and security solution from the beginning. I’ll explain why.
One of the primary reasons you’re making the move to Snowflake is to extract the maximum insights from your data to make better business decisions. You might start with anonymized datasets, but you’ll quickly need to include sensitive data to get the most insights, so why wait? The sooner you can run analytics on data that really matters, the faster you can deliver that value to the business. If you plan to do that from the beginning, that means preparing to comply with regulations around data privacy and protection. With new laws popping up across the US monthly, there’s no industry exempt from making sure data is safe from leaks and misuse. And there’s no lag to the risk – the day after you add the data, a trusted user could be phished or data could be misused, violating regulations.
Snowflake delivers the enterprise class security we all expect from leading cloud providers as well as some crucial features for protecting sensitive data, with more added in each new release. However, executing and managing those features must be done manually via SQL code – limiting the number of people who can implement and update policies, restricting your ability to scale easily as your project ramps up with new users and more data.
And, even Snowflake will tell you that it can’t be responsible for who has access, what data you include, or controlling how those two intersect: who should have access to what data. This means there’s no mechanism to stop credentialed access threats or privileged access to sensitive data – if someone has the right log in information, they can take as much data as they like. It’s on you to have a solution in place to stop this.
“Snowflake has a phenomenal security team, world class security posture, but there’s still responsibility on the customer to keep the account secure. And if a user is compromised…there have to be controls in place on the customer’s side to detect that’s happened and to be able to remediate that quickly before the sensitive data gets out,” Omer Singer, Head of Cyber Security Strategy at Snowflake.

Consider ALTR a light addition to your pack that helps you move more quickly down the road:
The best thing you can do for your business is accelerate your adoption of your cloud data platform so you can drive business value faster. Imagine six months down the road, you’re two years ahead of where you hoped to be. Planning your trip right from the start can enable you to do that. You eliminate the need to come to a screeching halt a few months in to think about how to manage data governance and security.
You can keep moving ahead of the speed of your business, leading the way to maximum data value, when you include ALTR from the start.


A few weeks ago I attended the Gartner Security and Risk Summit in Washington, DC, where ALTR was sponsoring and meeting with analysts, customers, and prospects (ALTR is a Gartner client). As usual it was really interesting to see how the overall market is evolving and where the focus is. Here are a few of the major themes that I observed:
Automation as the way to cope with increasing complexity and a persistent labor shortfall. The opening keynote by Gartner focused pretty heavily here. I believe the key stat is that 70% of companies reported that they can’t even digest 60% of their event traffic (from a SIEM or SOAR perspective), meaning they actually aren’t watching parts of their network at all, despite all of the investment in tools. And that just gets worse when you consider that hiring to fill that gap is getting harder to do, not easier.
My take: I am reluctant here – the idea of automation is much simpler than the execution, and I am skeptical of this technology’s ability to close this gap. Today’s automation has very little real predictive ability, and often produces as much work in training and managing false positives as it does in saving work. I think the answer here is to focus what we are monitoring based on risk, not monitor everything and just turn it over to automation.
Identity is the new perimeter. This theme was dominant throughout and focuses on the fact that in today’s cloud-powered and mobile world, the traditional network perimeter has dissolved and been replaced by authentication and access management. It’s notable that user credentials are now far and away the most popular attack vector for bad actors, from credential-stuffing to phishing credentials out of users via email and other avenues.
My take: I agree. I think you must verify, and then re-verify that the person who is accessing resources is in fact who they say they are. Some encouraging statistics are that something simple like multi-factor authentication will stop 97% of credential-based attacks. Of course, even then that 3% is still a really large number in absolute terms, and pretty troubling.
Identity and data will always be your problem. A lot of the conference was about cloud security, and I saw some great sessions about trends in this space. But the thing that I found really compelling was a particular chart that showed how when you go from IaaS to PaaS to SaaS, you shed responsibilities for various parts of the stack . . . but managing identity and data remain your responsibility.
My take: I think this view was compelling because it separates the IT-driven benefits of cloud computing from the risks that holding data can pose, and makes the point that those risks are still there no matter where your application workloads and databases are hosted.
The rise of Data Security Governance. Gartner publishes a model on data security governance that is meant to focus on a risk-based approach to managing data across both security and privacy concerns. The emphasis is not to start with security products, but to consider data more broadly. This framework was present throughout the conference in various sessions.
My take: I think this is absolutely the right approach. Once you authenticate someone it is important to manage what data they have access to globally. However as with most great strategic concepts it has problems when it meets the real world. The “product first” mentality is driven by the fact that data security and governance products are isolated from each other in different quadrants like DLP or CASB tools and in market guides like DCAP, Tokenization, and Data Masking. I sense an opportunity for Gartner to collapse products into a Data Security Governance market that gives organizations more of a connection between the risks and the tools that address them. I believe that some of these tools, and even some of these categories, don’t actually do that much to decrease the risk to data – and Gartner could help clients differentiate the good investments from the not as good.

Say you’re in a busy train station, looking for a store that sells water, and you spot someone handing out water for free. If you’re anything like me (read: paranoid), your first instinct is “This is either a charity or it’s a scam” and “Will that water make me sick?” Now imagine if the train station is the internet, and you’re looking for a service provider in the already sensitive space of data privacy. Alarm bells are definitely going off!
This might be caused by instinctual responses we have to the idea of a “free” product or solution. Even if (or especially if!) something seems genuinely disruptive like Amazon’s free delivery or Southwest’s no-fee changes, we could be skeptical. The value to us may seem obvious, but we wonder what’s in it for the vendor. What’s the catch?
So, let’s talk about where those reactions come from and see if they hold true for today’s free business software, especially SaaS solutions.
Simple economics has taught us that the higher priced a product is, the higher quality you should expect from it. This isn’t a hard and fast rule - sometimes we get fooled into paying for a brand or a logo - but it’s why you may not have a problem paying more for premium items, such organic foods or luxury goods. And when you go “cheap”, you generally accept lower quality and the consequences of that. Fast fashion is meant to be replaced yearly, and there’s a reason people celebrate moving on from furniture you put together yourself.
However, software is not the same as consumer goods – the same pricing structure doesn’t apply. With the technologies we have today, Software-as-a-Service (SaaS) companies can build software that solves problems common to multiple companies, then simply serve up that same solution to customer after customer directly from the cloud. They can deliver those benefits to a significant slice of the market without requiring costly customizations, consultant implementation hours or onsite hardware installations. This allows companies built on SaaS from the ground up, with a business model just as streamlined and flexible, to leverage efficiencies of scale to offer powerful software at a much lower cost than legacy on-premises providers. You can’t do that with clothes or furniture. ALTR VP of Product Doug Wick explained very clearly how being built on the cloud from the beginning helps ALTR to deliver our solutions more quickly and for a lower cost than legacy on-premises solutions.
I’d go even further: not only is free software not necessarily lower quality, it actually has to deliver even higher quality than a paid solution in order to retain and grow the customer base. Because there’s no financial commitment by the user, it’s easy to start but just as easy to stop using the product. A free tool quickly exposes any weaknesses, issues or flaws. Users will need a seamless experience that delivers value immediately in order to continue, let alone consider upgrading to a paid version.
This idea has been around a while, but really took off during the Facebook/Cambridge Analytica scandal. Many of us jumped onboard the Facebook train, adding our contacts, sharing our updates, checking in at locations – enjoying the opportunity to use technology to be more closely connected to our far-flung network. But most of us may not have considered what was happening with all that data. It turns out that our data is a commodity. We learned through scandal to be skeptical, and Facebook is far from alone. For example, a popular email cleanup tool turned out to be using the opportunity to collect and sell information on user purchases. In fact, a company co-founder accused users of being “naïve” to think the tool wasn’t “monetizing” their data.
This is especially threatening for IT and security folks whose primary goal is to protect data! We know this feeling, as our founders come from data security in the financial services industry. They created ALTR to solve the problem of data control and privacy across the data ecosystem and built the company on a culture of data security.
When users sign up for ALTR’s free plan, what we’re getting is not your data (we don’t need to store it in order to protect it - it’s as secure as ever) but information about your experience. A free plan allows us to greatly expand our user base and gain more insight into how the software can best solve problems and provide a better experience. Our users become active participants in our product development process, helping make the platform work better for them and future users. It’s a win/win.
In the beginning, there was only enterprise software because only enterprises could afford it. It was developed to manage processes across the business, taking on big, complex problems on a massive scale. This came with expensive, years-long development cycles, complicated on-premises implementations by costly consultants, a big contractual commitment and a hefty price tag. The side effect was that even simple business problems could stay unsolved for months or years as the convoluted buying process wound its way along.
Today, business solutions are taking their lead from consumer software: focusing on individual user needs and experiences instead of tackling enterprise-sized challenges out of the gate. Companies like Slack, Zoom, Canva, and even Google offer low-cost or free versions of their software for messaging, design, or content development. This allows individual users at large enterprises to test-drive solutions to solve a specific thorny issue, making overall processes more efficient.
Instead of needing buy-in from an endless number of executives and months-long contract negotiations followed by months- or years-long implementations, the users who will actually be using the software can simply sign up and try it. Once they understand intuitively how it works and determine if it will solve the problem, they can share with others throughout the organization for their review. If it gets traction, it’s much easier to upgrade to an enterprise-level subscription for additional features or support or to take on larger challenges across the business. This is buying from the ground up instead of the top down.
ALTR’s free plan, for example, lets governance and data teams identify sensitive data in Snowflake, see who’s using it, and put basic access controls in place. It allows companies with a smaller need to address it immediately and users at larger orgs get a taste of how the solution would scale across all their data. A clear upgrade path makes it easy to grow as needed.
So, while low cost or free may seem suspicious when it comes to clothes or furniture (or bottles of water!), software is a different beast. Technology advances have disrupted the way software is developed and the usefulness it can deliver to business users for low or even no investment. For those who associate free products with a drop in value or quality, it’s time to reconsider our general impulses around pricing to ensure you're not missing out on the real opportunity.


We recently sat down with Fred Burton, a member of ALTR’s board of advisors, to hear his perspective on the landscape of threats to enterprise data security and integrity. Burton heads the global security practice of Stratfor. Before Stratfor, he was a counterterrorism agent for the U.S. State Department and leader of many high profile international investigations. He is an author whose four books include the best-selling “GHOST: Confessions of a Counterrorism Agent.”
BURTON: Well, the first line of concern has always been the insider threat. And that threat has been transformed by an order of magnitude through the transformation of information storage from paper and filing cabinets to servers and the cloud. In the government space in particular, we had plenty of insider threats in the 1950s, 1960s and 1970s, but there were limits to how many 201 files as we called them (source and personnel files) that you could walk out with in a briefcase or what you could photograph with a tiny Minox camera. Now even the ease of theft enabled by a memory stick is growing old as thievery is conducted from across the globe with stolen goods finding a ready market on the dark web. In today’s digital economy, the bad guys don’t even need to get out of their pajamas anymore.
BURTON: Actually, I think of it not in terms of the interplay of two categories of insider threat but three categories. For starters, you’ve got the need for digital solutions, be those at the heart of the data ecosystem as with ALTR or older solutions focused on the network or network endpoints.
The second category is what I call situational awareness. This is the training, the enforcement of internal security policies, the general commitment to security hygiene if you will. There’s a role of growing importance for HR to play in every enterprise. The last category that could use some more attention is the threat of intellectual property that can leak out of the C-suite if not protected by NDAs, policies for talent retention and ethics standards. Everybody’s chasing top talent these days and your most talented are usually reservoirs of knowledge about data if not data itself. This is where legal departments really need to step up their game.
BURTON: Well, cyber and data security is on the minds of just about every executive I talk to, from medium-sized domestic firms to global multinationals. And everyone is looking for a quick magic potion, a simplistic, brass ring of a solution that can be put on autopilot and spit out the next Edward Snowden before he’s done anything. What I think is more realistic and useful are security concepts that reduce and mitigate risks and those that quickly stem the bleeding when injury occurs. We need to think in terms of cocktail solutions and less about silver bullets.
BURTON: This follows really on my points about managing three categories of threats and the elusive hunt for magic potions. Enterprises need to be thinking broadly, not narrowly. But when it comes to action, it’s a similar kind of comprehensiveness in the solution architecture that is one of the things that appealed to me about ALTR’s technology from the first day I saw it. It’s not just about fire alarms to alert you to the conflagration – though you need those too. It’s about the smoke alarms that alert you before the fire actually erupts in flames and before the damage can spread. As a former investigator, you can well imagine that ALTR’s quick sand as I call it, the picture of digital truth that immutability records virtually all behavior in the interaction of personnel with data, is a very powerful and valuable tool. It’s this immutability enabled by blockchain that I believe is really critical to secure the future of the data economy.
BURTON: I worry a great deal about systemic threats, the risks to the ecosystem of distinct businesses. It relates to our discussion of the transformation in a very short time from a world of filing cabinets to a world of cloud-based information measured in terabytes of data. And if enterprises need to spot the smoke before the fire, then business ecosystems need to spot the brush fire before it engulfs the entire forest. It’s not enough, sadly, for any enterprise to have its own house in order. If data integration along the supply chain is not protected, if vendors are breached or sales partners are careless, the result can be domino effects. From banking to hospitals to power grids, the potential of the domino effect is real and growing. And the fastest growing dimension of the overall threat matrix is, of course, the Internet of Things, IoT, that will be woven into the fabric of every enterprise. This is just one element of this that really does keep me up at night. It’s not a figure of speech.
BURTON: Think holistically. That’s the key in my view. A holistic approach to security, of course, needs to include the old school elements: hiring practices, an eye on personnel issues that may lead to desperation and carefully written contracts and NDAs. But far beyond that, the technology we use to confront threats to data, particularly insider threats, needs to be comprehensive and holistic. We need technology that protects data from being breached. But just building bigger walls and moats around the castle, which is where a great deal of thinking is stuck today, is not enough. To carry the analogy, we also need to know what’s going on inside the castle. We need deft use of technology that allows real time monitoring of data access, use and consumption. This is critical not only to enforcing policy on data, but also to establish policy. And lastly, as I mentioned, we need tools that yield a mitigation roadmap, a picture of digital truth, if and when a breach is attempted. This is the cocktail approach we need to embrace. Without this new tool set and attitude, risk mitigation and management is akin to a surgeon practicing without the benefit of X-rays.

It’s been a little more than six months since we announced our direct cloud integration with Snowflake, and during that time the cloud data platform environment has only continued to heat up. In June, Snowflake's third annual user conference brought a focus on Global Data Governance as one of the platform’s five key pillars and with that, new capabilities like anonymized views and PII classification. And the company’s just announced Q2 results reflect its continued importance in the market with 103% year-over-year growth.
In the six months since the release of our integration, ALTR has added new joint customers including HumanN, The Zebra and Welltok. And we’ve utilized Snowflake’s native features like masking policies and external functions to deliver unique solutions to our shared customers.
Tarik Dwiek, Head of Technology Alliances at Snowflake, said,
“ALTR is an innovator in using Snowflake’s extensibility features. By utilizing these features, they’re able to deliver powerful data protection and security natively integrated, allowing our customers to get more value from their Snowflake investment.”
We’ll continue to leverage new native capabilities to tackle crucial data governance and security challenges for our customers as they move to Snowflake.
A Security-First Approach to Re-Platforming Data in the Cloud
Q2's Chief Availability Officer Lou Senko, Snowflake's Head of Cyber Security Strategy Omer Singer, and ALTR CTO James Beecham discuss how innovative organizations like Q2 are taking a security-first approach to migrating from on-premises databases to cloud data warehouses, mitigating risk while maximizing their data strategy.
Do You Know What Your Tableau Users Are Doing in Snowflake?
When companies use a shared service account for Tableau access to Snowflake, it becomes impossible to see and control sensitive data access by individual users. ALTR solves this with some sophisticated development in our platform that requires just a simple change in Tableau to activate. See how Snowflake DBAs can configure and manage one Tableau service account, yet get per user visibility and governance as if every end user had their own account.
Humann Utilizes Data Consumption Intelligence to Better Govern Customer Data
Customer-centric hyper growth company HumanN is focused on creating and delivering superior functional nutrition products for the health and fitness industry. Because customer outreach is a large part of its mission, the company holds a significant amount of customer personally identifiable information (PII) in Snowflake so protecting that data was essential to maintaining compliance and trust. See how ALTR helped with sensitive data discovery, consumption visibility, and purpose-based access control in Snowflake, all less than 40 days.
Plowing Through Data Governance Challenges and Security Risks on the Road to Snowflake
Our Director of Customer Success and Support, Jennifer Owens, works with companies to understand their challenges and help them build a plan to achieve their goals by utilizing the Snowflake + ALTR native solution. Here she shares use cases around securing consolidated enterprise data, enabling compliant PHI sharing, securing highly sensitive data and more.
Moving to the Cloud Doesn't Have to Be Daunting for Small and Mid-size Financial Institutions
Small- and mid-size financial institutions might think moving to the cloud is a huge lift or a big risk, but it doesn’t have to be. ALTR Account Director Paul Franz explains how you can move your enterprise data warehouse to the cloud, easily and safely with Snowflake + ALTR’s “secure cloud data warehouse-in-a-box”.
Snowflake Data Governance Buying Guide
Wherever you are in your Snowflake journey, it’s never too early or too late to think about how to handle sensitive data governance and security. But, it’s not always clear how the options stack up and what you really need. We put together this buying guide to help you understand the differences that really matter and what questions you should be asking as you evaluate your next move.
It’s been an amazing six months, but like a lot of you, we feel like we’re just getting started on our Snowflake journey. And we can’t wait for the next step!