Format-Preserving Encryption: A Deep Dive into FF3-1 Encryption Algorithm




In the ever-evolving landscape of data security, protecting sensitive information while maintaining its usability is crucial. ALTR’s Format Preserving Encryption (FPE) is an industry disrupting solution designed to address this need. FPE ensures that encrypted data retains the same format as the original plaintext, which is vital for maintaining compatibility with existing systems and applications. This post explores ALTR's FPE, the technical details of the FF3-1 encryption algorithm, and the benefits and challenges associated with using padding in FPE.
Format Preserving Encryption is a cryptographic technique that encrypts data while preserving its original format. This means that if the plaintext data is a 16-digit credit card number, the ciphertext will also be a 16-digit number. This property is essential for systems where data format consistency is critical, such as databases, legacy applications, and regulatory compliance scenarios.
The FF3-1 encryption algorithm is a format-preserving encryption method that follows the guidelines established by the National Institute of Standards and Technology (NIST). It is part of the NIST Special Publication 800-38G and is a variant of the Feistel network, which is widely used in various cryptographic applications. Here’s a technical breakdown of how FF3-1 works:
1. Feistel Network: FF3-1 is based on a Feistel network, a symmetric structure used in many block cipher designs. A Feistel network divides the plaintext into two halves and processes them through multiple rounds of encryption, using a subkey derived from the main key in each round.
2. Rounds: FF3-1 typically uses 8 rounds of encryption, where each round applies a round function to one half of the data and then combines it with the other half using an XOR operation. This process is repeated, alternating between the halves.
3. Key Scheduling: FF3-1 uses a key scheduling algorithm to generate a series of subkeys from the main encryption key. These subkeys are used in each round of the Feistel network to ensure security.
4. Tweakable Block Cipher: FF3-1 includes a tweakable block cipher mechanism, where a tweak (an additional input parameter) is used along with the key to add an extra layer of security. This makes it resistant to certain types of cryptographic attacks.
5. Format Preservation: The algorithm ensures that the ciphertext retains the same format as the plaintext. For example, if the input is a numeric string like a phone number, the output will also be a numeric string of the same length, also appearing like a phone number.
1. Initialization: The plaintext is divided into two halves, and an initial tweak is applied. The tweak is often derived from additional data, such as the position of the data within a larger dataset, to ensure uniqueness.
2. Round Function: In each round, the round function takes one half of the data and a subkey as inputs. The round function typically includes modular addition, bitwise operations, and table lookups to produce a pseudorandom output.
3. Combining Halves: The output of the round function is XORed with the other half of the data. The halves are then swapped, and the process repeats for the specified number of rounds.
4. Finalization: After the final round, the halves are recombined to form the final ciphertext, which maintains the same format as the original plaintext.
Implementing FPE provides numerous benefits to organizations:
1. Compatibility with Existing Systems: Since FPE maintains the original data format, it can be integrated into existing systems without requiring significant changes. This reduces the risk of errors and system disruptions.
2. Improved Performance: FPE algorithms like FF3-1 are designed to be efficient, ensuring minimal impact on system performance. This is crucial for applications where speed and responsiveness are critical.
3. Simplified Data Migration: FPE allows for the secure migration of data between systems while preserving its format, simplifying the process and ensuring compatibility and functionality.
4. Enhanced Data Security: By encrypting sensitive data, FPE protects it from unauthorized access, reducing the risk of data breaches and ensuring compliance with data protection regulations.
5. Creation of production-like data for lower trust environments: Using a product like ALTR’s FPE, data engineers can use the cipher-text of production data to create useful mock datasets for consumption by developers in lower-trust development and test environments.
Padding is a technique used in encryption to ensure that the plaintext data meets the required minimum length for the encryption algorithm. While padding is beneficial in maintaining data structure, it presents both advantages and challenges in the context of FPE:
1. Consistency in Data Length: Padding ensures that the data conforms to the required minimum length, which is necessary for the encryption algorithm to function correctly.
2. Preservation of Data Format: Padding helps maintain the original data format, which is crucial for systems that rely on specific data structures.
3. Enhanced Security: By adding extra data, padding can make it more difficult for attackers to infer information about the original data from the ciphertext.
1. Increased Complexity: The use of padding adds complexity to the encryption and decryption processes, which can increase the risk of implementation errors.
2. Potential Information Leakage: If not implemented correctly, padding schemes can potentially leak information about the original data, compromising security.
3. Handling of Padding in Decryption: Ensuring that the padding is correctly handled during decryption is crucial to avoid errors and data corruption.
ALTR's Format Preserving Encryption, powered by the technically robust FF3-1 algorithm and married with legendary ALTR policy, offers a comprehensive solution for encrypting sensitive data while maintaining its usability and format. This approach ensures compatibility with existing systems, enhances data security, and supports regulatory compliance. However, the use of padding in FPE, while beneficial in preserving data structure, introduces additional complexity and potential security challenges that must be carefully managed. By leveraging ALTR’s FPE, organizations can effectively protect their sensitive data without sacrificing functionality or performance.
For more information about ALTR’s Format Preserving Encryption and other data security solutions, visit the ALTR documentation

For years (even decades) sensitive information has lived in transactional and analytical databases in the data center. Firewalls, VPNs, Database Activity Monitors, Encryption solutions, Access Control solutions, Privileged Access Management and Data Loss Prevention tools were all purchased and assembled to sit in front of, and around, the databases housing this sensitive information.
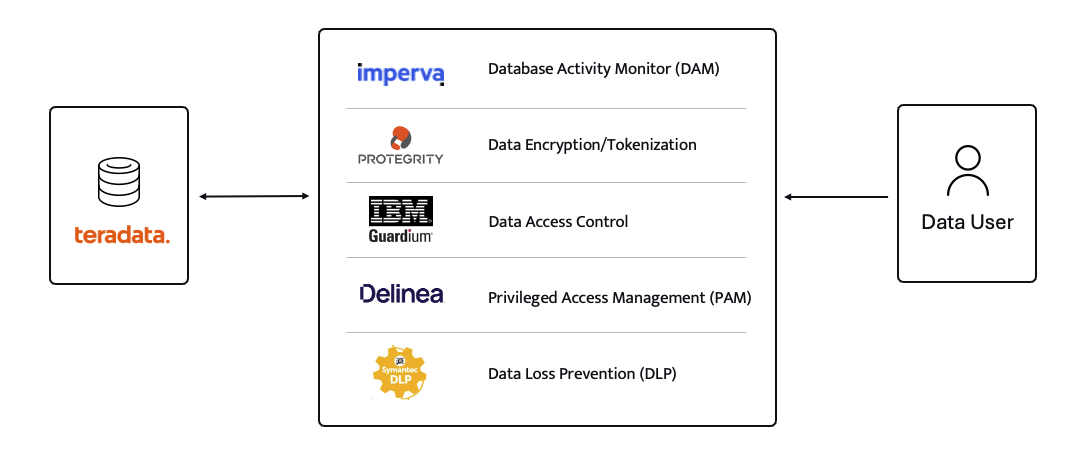
Even with all of the above solutions in place, CISO’s and security teams were still a nervous wreck. The goal of delivering data to the business was met, but that does not mean the teams were happy with their solutions. But we got by.
The advent of Big Data and now Generative AI are causing businesses to come to terms with the limitations of these on-prem analytical data stores. It’s hard to scale these systems when the compute and storage are tightly coupled. Sharing data with trusted parties outside the walls of the data center securely is clunky at best, downright dangerous in most cases. And forget running your own GenAI models in your datacenter unless you can outbid Larry, Sam, Satya, and Elon at the Nvidia store. These limits have brought on the era of cloud data platforms. These cloud platforms address the business needs and operational challenges, but they also present whole new security and compliance challenges.
ALTR’s platform has been purpose-built to recreate and enhance these protections required to use Teradata for Snowflake. Our cutting-edge SaaS architecture is revolutionizing data migrations from Teradata to Snowflake, making it seamless for organizations of all sizes, across industries, to unlock the full potential of their data.
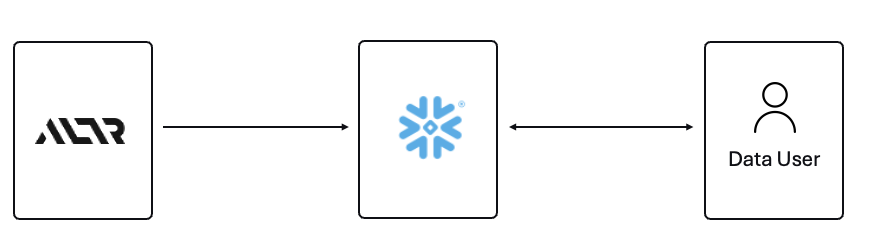
What spurred this blog is that a company reached out to ALTR to help them with data security on Snowflake. Cool! A member of the Data & Analytics team who tried our product and found love at first sight. The features were exactly what was needed to control access to sensitive data. Our Format-Preserving Encryption sets the standard for securing data at rest, offering unmatched protection with pricing that's accessible for businesses of any size. Win-win, which is the way it should be.
Our team collaborated closely with this person on use cases, identifying time and cost savings, and mapping out a plan to prove the solution’s value to their organization. Typically, we engage with the CISO at this stage, and those conversations are highly successful. However, this was not the case this time. The CISO did not want to meet with our team and practically stalled our progress.
The CISO’s point of view was that ALTR’s security solution could be completely disabled, removed, and would not be helpful in the case of a compromised ACCOUNTADMIN account in Snowflake. I agree with the CISO, all of those things are possible. Here is what I wanted to say to the CISO if they had given me the chance to meet with them!
The ACCOUNTADMIN role has a very simple definition, yet powerful and long-reaching implications of its use:

One of the main points I would have liked to make to the CISO is that as a user of Snowflake, their responsibility to secure that ACCOUNTADMIN role is squarely in their court. By now I’m sure you have all seen the news and responses to the Snowflake compromised accounts that happened earlier this year. It is proven that unsecured accounts by Snowflake customers caused the data theft. There have been dozens of articles and recommendations on how to secure your accounts with Snowflake and even a mandate of minimum authentication standards going forward for Snowflake accounts. You can read more information here, around securing the ACCOUNTADMIN role in Snowflake.
I felt the CISO was missing the point of the ALTR solution, and I wanted the chance to explain my perspective.
ALTR is not meant to secure the ACCOUNTADMIN account in Snowflake. That’s not where the real risk lies when using Snowflake (and yes, I know—“tell that to Ticketmaster.” Well, I did. Check out my write-up on how ALTR could have mitigated or even reduced the data theft, even with compromised accounts). The risk to data in Snowflake comes from all the OTHER accounts that are created and given access to data.
The ACCOUNTADMIN role is limited to one or two people in an organization. These are trusted folks who are smart and don’t want to get in trouble (99% of the time). On the other hand, you will have potentially thousands of non-ACCOUNTADMIN users accessing data, sharing data, screensharing dashboards, re-using passwords, etc. This is the purpose of ALTR’s Data Security Platform, to help you get a handle on part of the problem which is so large it can cause companies to abandon the benefits of Snowflake entirely.
There are three major issues outside of the ACCOUNTADMIN role that companies have to address when using Snowflake:
1. You must understand where your sensitive is inside of Snowflake. Data changes rapidly. You must keep up.
2. You must be able to prove to the business that you have a least privileged access mechanism. Data is accessed only when there is a valid business purpose.
3. You must be able to protect data at rest and in motion within Snowflake. This means cell level encryption using a BYOK approach, near-real-time data activity monitoring, and data theft prevention in the form of DLP.
The three issues mentioned above are incredibly difficult for 95% of businesses to solve, largely due to the sheer scale and complexity of these challenges. Terabytes of data and growing daily, more users with more applications, trusted third parties who want to collaborate with your data. All of this leads to an unmanageable set of internal processes that slow down the business and provide risk.
ALTR’s easy-to-use solution allows Virgin Pulse Data, Reporting, and Analytics teams to automatically apply data masking to thousands of tagged columns across multiple Snowflake databases. We’re able to store PII/PHI data securely and privately with a complete audit trail. Our internal users gain insight from this masked data and change lives for good.
- Andrew Bartley, Director of Data Governance
I believed the CISO at this company was either too focused on the ACCOUNTADMIN problem to understand their other risks, or felt he had control over the other non-admin accounts. In either case I would have liked to learn more!
There was a reason someone from the Data & Analytics team sought out a product like ALTR. Data teams are afraid of screwing up. People are scared to store and use sensitive data in Snowflake. That is what ALTR solves for, not the task of ACCOUNTADMIN security. I wanted to be able to walk the CISO through the risks and how others have solved for them using ALTR.
The tools that Snowflake provides to secure and lock down the ACCOUNTADMIN role are robust and simple to use. Ensure network policies are in place. Ensure MFA is enabled. Ensure you have logging of ACCOUNTADMIN activity to watch all access.
I wish I could have been on the conversation with the CISO to ask a simple question, “If I show you how to control the ACCOUNTADMIN role on your own, would that change your tone on your teams use of ALTR?” I don’t know the answer they would have given, but I know the answer most CISO’s would give.
Nothing will ever be 100% secure and I am by no means saying ALTR can protect your Snowflake data 100% by using our platform. Data security is all about reducing risk. Control the things you can, monitor closely and respond to the things you cannot control. That is what ALTR provides day in and day out to our customers. You can control your ACCOUNTADMIN on your own. Let us control and monitor the things you cannot do on your own.

Since 2015 the migration of corporate data to the cloud has rapidly accelerated. At the time it was estimated that 30% of the corporate data was in the cloud compared to 2022 where it doubled to 60% in a mere seven years. Here we are in 2024, and this trend has not slowed down.
Over time, as more and more data has moved to the cloud, new challenges have presented themselves to organizations. New vendor onboarding, spend analysis, and new units of measure for billing. This brought on different cloud computer-related cost structures and new skillsets with new job titles. Vendor lock-in, skill gaps, performance and latency and data governance all became more intricate paired with the move to the cloud. Both operational and transactional data were in scope to reap the benefits promised by cloud computing, organizational cost savings, data analytics and, of course, AI.
The most critical of these new challenges revolve around a focus on Data Security and Privacy. The migration of on-premises data workloads to the Cloud Data Warehouses included sensitive, confidential, and personal information. Corporations like Microsoft, Google, Meta, Apple, Amazon were capturing every movement, purchase, keystroke, conversation and what feels like thought we ever made. These same cloud service providers made this easier for their enterprise customers to do the same. Along came Big Data and the need for it to be cataloged, analyzed, and used with the promise of making our personal lives better for a cost. The world's population readily sacrificed privacy for convenience.
The moral and ethical conversation would then begin, and world governments responded with regulations such as GDPR, CCPA and now most recently the European Union’s AI Act. The risk and fines have been in the billions. This is a story we already know well. Thus, Data Security and Privacy have become a critical function primarily for the obvious use case, compliance, and regulation. Yet only 11% of organizations have encrypted over 80% of their sensitive data.
With new challenges also came new capabilities and business opportunities. Real time analytics across distributed data sources (IoT, social media, transactional systems) enabling real time supply chain visibility, dynamic changes to pricing strategies, and enabling organizations to launch products to market faster than ever. On premise applications could not handle the volume of data that exists in today’s economy.
Data sharing between partners and customers became a strategic capability. Without having to copy or move data, organizations were enabled to build data monetization strategies leading to new business models. Now building and training Machine Learning models on demand is faster and easier than ever before.
To reap the benefits of the new data world, while remaining compliant, effective organizations have been prioritizing Data Security as a business enabler. Format Preserving Encryption (FPE) has become an accepted encryption option to enforce security and privacy policies. It is increasingly popular as it can address many of the challenges of the cloud while enabling new business capabilities. Let’s look at a few examples now:
Real Time Analytics - Because FPE is an encryption method that returns data in the original format, the data remains useful in the same length, structure, so that more data engineers, scientists and analysts can work with the data without being exposed to sensitive information.
Data Sharing – FPE enables data sharing of sensitive information both personal and confidential, enabling secure information, collaboration, and innovation alike.
Proactive Data Security– FPE allows for the anonymization of sensitive information, proactively protecting against data breaches and bad actors. Good holding to ransom a company that takes a more proactive approach using FPE and other Data Security Platform features in combination.
Empowered Data Engineering – with FPE data engineers can still build, test and deploy data transformations as user defined functions and logic in stored procedures or complied code will run without failure. Data validations and data quality checks for formats, lengths and more can be written and tested without exposing sensitive information. Federated, aggregation and range queries can still run without fail without the need for decryption. Dynamic ABAC and RBAC controls can be combined to decrypt at runtime for users with proper rights to see the original values of data.
Cost Management – While FPE does not come close to solving Cost Management in its entirety, it can definitely contribute. We are seeing a need for FPE as an option instead of replicating data in the cloud to development, test, and production support environments. With data transfer, storage and compute costs, moving data across regions and environments can be really expensive. With FPE, data can be encrypted and decrypted with compute that is a less expensive option than organizations' current antiquated data replication jobs. Thus, making FPE a viable cost savings option for producing production ready data in non-production environments. Look for a future blog on this topic and all the benefits that come along.
FPE is not a silver bullet for protecting sensitive information or enabled these business use cases. There are well documented challenges in the FF1 and FF3-1 algorithms (another blog on that to come). A blend of features including data discovery, dynamic data masking, tokenization, role and attribute-based access controls and data activity monitoring will be needed to have a proactive approach towards security within your modern data stack. This is why Gartner considers a Data Security Platform, like ALTR, to be one of the most advanced and proactive solutions for Data security leaders in your industry.
Securing sensitive information is now more critical than ever for all types of organizations as there have been many high-profile data breaches recently. There are several ways to secure the data including restricting access, masking, encrypting or tokenization. These can pose some challenges when using the data downstream. This is where Format Preserving Encryption (FPE) helps.
This blog will cover what Format Preserving Encryption is, how it works and where it is useful.
Whereas traditional encryption methods generate ciphertext that doesn't look like the original data, Format Preserving Encryption (FPE) encrypts data whilst maintaining the original data format. Changing the format can be an issue for systems or humans that expect data in a specific format. Let's look at an example of encrypting a 16-digit credit card number:

As you can see with a Standard Encryption type the result is a completely different output. This may result in it being incompatible with systems which require or expect a 16-digit numerical format. Using FPE the encrypted data still looks like a valid 16-digit number. This is extremely useful for where data must stay in a specific format for compatibility, compliance, or usability reasons.
Format Preserving Encryption in ALTR works by first analyzing the column to understand the input format and length. Next the NIST algorithm is applied to encrypt the data with the given key and tweak. ALTR applies regular key rotation to maximize security. We also support customers bringing their own keys (BYOK). Data can then selectively be decrypted using ALTR’s access policies.
FPE offers several benefits for organizations that deal with structured data:
1. Adds extra layer of protection: Even if a system or database is breached the encryption makes sensitive data harder to access.
2. Original Data Format Maintained: FPE preserves the original data structure. This is critical when the data format cannot be changed due to system limitations or compliance regulations.
3. Improves Usability: Encrypted data in an expected format is easier to use, display and transform.
4. Simplifies Compliance: Many regulations like PCI-DSS, HIPAA, and GDPR will mandate safeguarding, such as encryption, of sensitive data. FPE allows you to apply encryption without disrupting data flows or reporting, all while still meeting regulatory requirements.
FPE is widely adopted in industries that regularly handle sensitive data. Here are a few common use cases:
ALTR offers various masking, tokenization and encryption options to keep all your Snowflake data secure. Our customers are seeing the benefit of Format Preserving Encryption to enhance their data protection efforts while maintaining operational efficiency and compliance. For more information, schedule a product tour or visit the Snowflake Marketplace.

In a previous post, Jonathan Sander details the primary differences between a Data Security Posture Management (DSPM) solution and a Data Security Platform (DSP). He highlights that the most notable difference between a DSPM and a DSP is in the “policy definition and policy enforcement” aspects of a DSP. He explains that while some applications allow for simple API calls to manage access or security policies, such as removing a user’s group membership in Active Directory, implementing policy definition and enforcement at a deeper level for platforms like Snowflake becomes exceedingly challenging, if not impossible, for a DSPM.
Recent events have reignited my interest in understanding how ALTR distinguishes itself from a DSPM. The first event was the potential acquisition of Wiz by Google. Wiz, a cloud security posture management (CSPM) tool, is often confused with a DSPM. This has led customers to inquire about the differences between CSPM and DSPM and, subsequently, the distinctions between DSPM and DSP. Although the Wiz/Google deal fell through, it sparked an insightful discussion on Linkedin initiated by Pramod Gosavi from JupiterOne. I participated in this discussion, which delved into why Google should reconsider buying a tool like Wiz.
The other recent event that brings DSPM v DSP back into spotlight is the word ‘remediation’, which has been used by some DSPM providers lately. The word remediation in this context indicates a DSPMs ability to react to one of their findings. For example, a remediation might be removing a user’s access from a system or making a public-facing internet resource private. These types of remediations are simple and straightforward and should easily be achievable by a DSPM. But lately, some of the DSPM players have been making mention of remediations for platforms like Snowflake stating their platforms can do complex operations such as RBAC, data masking, and data security such as encryption or tokenization. This is where the analogy "All squares are rectangles, but not all rectangles are squares" comes in handy. In this scenario, the DSPM is the square, and the DSP is the rectangle. A DSP can perform all the functions of a DSPM, but a DSPM cannot perform all the functions of a DSP. Let me explain.
The largest difference between a DSPM and a DSP is not the type or number of data stores supported, or the workflows within the platforms, but rather the biggest difference is the integration methods with the data stores. DSP’s live in the line of fire. We sit in the hardest place a vendor can sit, in the critical path of data. It’s the only way a DSP can provide capabilities like real-time database activity monitoring (DAM), data encryption or tokenization, data loss prevention, and others. Without this position in the stack, our ability to stop, or remediate, an out of policy data access request is minimized.
DSPM’s on the other hand do not live in the critical path of data access. They often exist outside the normal access patterns connecting to systems such as databases or file shares without fear of latency or uptime. A DSP has the unfortunate burden of having to essentially match the uptimes and availability of the platforms they control, often requiring significant investments in engineering and operations that DSPM do not have. It's these requirements of uptime, throughput, and strict performance metrics that make it nearly impossible for a DSPM to offer value over a DSP when it comes to complex operations in a platform like Snowflake. Since a DSP is already in line with the systems they are controlling and protecting, it is conceivable that a DSP could offer a wide overlap of the features of a DSPM, if it wanted to.
For customers, this means taking the time to understand the specific challenges you need to address for platforms like Snowflake, particularly regarding access controls and security. The multiple layers of roles and attributes assigned to users, the vast amount of data that moves and transforms inside the Snowflake platform daily, and the performance requirements of encryption on your downstream application is complex. These are hard problems for any business. And solving these challenge is what is going to fully unlock the value of your Snowflake instance.
Be cautious of any DSPM that claims to solve the complex governance and security challenges of Snowflake effortlessly. Always request detailed case studies to validate their claims. While it's not necessarily impossible, these claims often resemble a square trying to fit into a rectangle.

Data is the fuel propelling modern business. From customer information to financial records, proprietary data forms the foundation upon which businesses operate and innovate. However, as companies grow and data volumes explode, securing this data becomes exponentially more complex. This is where the importance of scalability in data security comes into sharp focus.
Scalability in data security is not a luxury; it is a necessity. As organizations expand, they generate and collect vast amounts of data. This growth demands a data security solution that can scale seamlessly with the volume, velocity, and variety of data. Organizations expose themselves to heightened risks, increased vulnerabilities, and potential catastrophic breaches without scalable security measures.
To understand the nuances of scalable security, we must delve into its core pillars: flexibility, performance, automation, and comprehensive coverage.
Flexibility is the cornerstone of scalable security. A rigid security solution that cannot adapt to changing needs and expanding data environments is destined to fail. Scalable security solutions must be flexible enough to integrate with a wide array of data sources, applications, and infrastructures, whether on-premises, in the cloud, or hybrid environments.
Flexibility also means accommodating varying security policies and compliance requirements. As regulations evolve and new threats emerge, a scalable security platform must allow for rapid adjustments to policies and controls without disrupting operations.
As data volumes grow, maintaining performance is crucial. Security measures that introduce latency or degrade performance are counterproductive and can hinder business operations and user experience. Scalable data security solutions must be designed to handle high throughput and large-scale environments without compromising o speed or efficiency.
Performance in scalable security also involves optimizing resource utilization. Efficient use of computational resources ensures that security operations, such as encryption, decryption, and monitoring, do not become bottlenecks as data scales.
Automation is a critical component of scalability in data security. Manual processes are time-consuming, error-prone, and incapable of keeping up with the dynamic nature of modern data environments. For instance, manually writing and maintaining SQL queries for data access control can be labour-intensive and prone to mistakes. Scalable security platforms leverage automation to ensure continuous protection without requiring constant human intervention.
Automated access policies, tokenization, and policy enforcement allow organizations to scale their security operations in line with their data growth. This automation enhances security posture and frees up valuable human resources to focus on strategic initiatives.
Scalable security requires comprehensive coverage across all data assets and environments. It is insufficient to secure only certain parts of the data ecosystem while leaving others vulnerable. A genuinely scalable security solution provides end-to-end protection, encompassing data at rest, in transit, and use.
Comprehensive coverage also means detecting and mitigating threats across the entire attack surface. This includes monitoring for insider threats, external attacks, and vulnerabilities within the data infrastructure. Scalable security platforms employ advanced analytics and machine learning to provide real-time insights and proactive threat management.
The complexity of scalable security lies in its ability to balance the varying demands of growth, performance, and protection. Here are some critical nuances to consider:
Scalable security solutions must be designed with future growth in mind. This involves anticipating the increase in data volume and users, the evolution of threat landscapes, and regulatory requirements. Future-proofing ensures that security investments remain practical and relevant as the organization evolves.
Interoperability is critical in a diverse data ecosystem. Scalable security platforms must seamlessly integrate with existing tools, applications, and processes. This integration capability ensures that security measures do not operate in silos but rather enhance the overall security posture through cohesive and collaborative defenses.
As data scales, so do the costs associated with securing it. Scalable security solutions must provide a cost-effective approach to protection, balancing the need for robust security with budget constraints. One approach is to leverage native architectures to manage costs effectively.
The consequences of failing to implement scalable security measures are dire. As data grows unchecked by scalable security, organizations face an increased risk of data breaches, regulatory fines, and reputational damage. Here are some potential pitfalls:
Without scalable security, the likelihood of data breaches increases significantly. Cybercriminals exploit vulnerabilities in outdated or inadequate security measures, leading to unauthorized access, data theft, and financial losses.
Data protection regulations are becoming increasingly stringent. Organizations that fail to scale their security measures in accordance with these requirements risk non-compliance, which can result in hefty fines and legal repercussions.
Inadequate security stability can lead to operational disruptions. Performance bottlenecks, system downtime, and compromised data integrity can impede business operations, leading to loss of productivity and revenue. Additionally, when security measures fail to scale, legitimate users may be unable to access critical data, causing further delays and hindering decision-making processes. This not only frustrates employees but also hampers overall business efficiency and agility.
In a world where data is both a valuable asset and a potential liability, the importance of scalable security cannot be overstated. As businesses continue to expand and generate more data, the need for robust, scalable security measures will only become more critical. Embracing scalable security is about protecting data today and preparing for tomorrow's challenges. The time to act is now.

Imagine waking up to the news that your company's sensitive data has been compromised, all due to stolen credentials. With recent high-profile data breaches making headlines, this nightmare scenario has become all too real for many organizations. The stakes are higher than ever, and ensuring robust security measures to protect your sensitive data in Snowflake is not just important—it's essential.
Snowflake's white paper, "Best Practices to Mitigate the Risk of Credential Compromise," is your roadmap to fortified security. This comprehensive guide reveals how to leverage Snowflake's native platform features to enforce strong authentication and mitigate the ever-present risks associated with credential theft. This blog will dive into the key takeaways and best practices recommended by Snowflake to safeguard your organization's data.
Snowflake's approach to security is built on three key pillars:
Encourage users to adopt security best practices, such as configuring multifactor authentication (MFA). This proactive approach ensures that users are aware of security protocols and actively engage with them. It's about creating a culture of security and mindfulness.
Enable administrators to enforce security measures by default. This means implementing policies that automatically apply security best practices across the board, reducing the likelihood of human error or oversight.
Provide visibility into security policy adherence. Monitoring ensures that security measures are not just in place but are being followed and are effective. Continuous visibility allows for timely adjustments and responses to potential threats.
By grounding its security framework in these pillars, Snowflake ensures a comprehensive approach to protecting sensitive data from unauthorized access.
To safeguard your Snowflake account, it's crucial to follow these essential steps:
Use key pair or OAuth for programmatic access and enforce this through authentication policies. Service accounts, which are often targeted by attackers, should have the most stringent security measures. By using key pairs or OAuth, you ensure a higher security level than traditional username/password combinations.
Leverage your own SAML identity providers with MFA solutions. For added security, enforce Snowflake's native MFA for users relying on native passwords. MFA adds an additional layer of security, making it significantly harder for attackers to gain access using stolen credentials.
Implement stringent password requirements and regular password changes. Strong passwords and regular updates reduce the risk of password-based attacks. Policies should include guidelines on password complexity and the frequency of changes.
Define policies to enforce reauthentication after periods of inactivity. This helps to minimize the risk of unauthorized access from inactive sessions. Policies should specify session timeout periods and conditions for reauthentication.
Restrict access to authorized and trusted sources only. By defining network policies, you can ensure that only trusted IP addresses and networks can access your Snowflake account, reducing the attack surface.
Differentiate between human and service users by setting user types, which helps in applying appropriate security measures. Service users often have elevated permissions, making them prime targets for attacks. By categorizing them appropriately, you can apply stricter security controls.
Apply password and session policies at the account level and test service users to ensure their effectiveness. Regular testing and validation of policies help identify potential gaps and ensure that security measures are working as intended.
Apply MFA enforcement policies to ensure all human interactive users use MFA. This universal application of MFA ensures that every user accessing the system is authenticated through multiple factors, significantly enhancing security.
Utilize Snowflake's Trust Center to monitor MFA and network policy enforcement continuously. Monitoring helps maintain a robust security posture by providing insights into policy adherence and identifying areas for improvement. Additionally, consider CIS benchmarks for industry-standard security practices and guidelines.
The digital landscape is fraught with threats, and credential compromise remains a top concern for organizations. Implementing the best practices outlined here is your first line of defense. However, it's not enough to set these measures and forget them. Continuous vigilance, regular updates, and a proactive stance are crucial.
Snowflake is your ally in this ongoing battle, providing the necessary tools and insights to effectively monitor and enforce security policies. By leveraging Snowflake's robust security framework, you can ensure your organization stays ahead of potential threats.
.png)
In today's hyper-connected world, businesses thrive on data. Every transaction, customer interaction, and strategic decision is driven by the vast amounts of information collected and stored. This data fuels innovation, enhances customer experiences, and propels growth. Yet, with this immense power comes a chilling reality: data breaches are an ever-present threat. From stolen customer information to compromised intellectual property, the consequences for businesses can be catastrophic. As these threats escalate, the burning question remains - how much data security is truly enough for your business?
Imagine a bank vault guarded by the most advanced security system. This is the traditional security mindset – an impenetrable fortress. However, cyberattacks are a relentless foe, constantly evolving to exploit new vulnerabilities faster than patches can be deployed. No system is truly invincible.
The ideal security system for a business might resemble Fort Knox, but that's not practical for everyday operations. Requiring retinal scans, fingerprints, voice verification, and a complex 30-character password just to access your company's internal systems would be excessively secure but also frustrating and inefficient for employees. Striking a balance between robust security and user-friendly access controls is crucial for businesses to navigate the security-usability tightrope effectively. Companies must implement security measures that protect sensitive data without impeding productivity or causing undue stress for users.
Investing in a million-dollar security system might make sense for a financial institution safeguarding sensitive data, but it would be overkill for a small business.Security measures come with a price tag – software, hardware, and trained personnel. The cost of these measures must be weighed against the potential damage of a breach. Prioritizing security investments based on the specific risks and needs of the business is crucial to ensure that resources are used effectively and efficiently. Companies must find the right balance between adequate protection and financial feasibility.
Imagine a trusted employee leaking sensitive data. Even the most sophisticated security cannot defend against disgruntled employees or social engineering attacks. Human error and malicious intent are ever-present dangers. Security awareness training and a culture of data responsibility are essential.
Hackers continuously shift tactics from brute-force attacks to phishing campaigns exploiting software vulnerabilities. As these threats evolve, security measures must also be dynamic and adaptable. Businesses must treat security as a fluid process, constantly changing to counter new and emerging threats effectively. This continuous adaptation is essential for staying ahead in the ever-changing landscape of cyber threats.
Not all data is created equal. Financial records, medical information, and intellectual property require the highest level of security. Less sensitive data, like movie preferences, can be protected with less stringent measures. Security needs to be tailored based on data value.
Perhaps it's not about achieving "enough" security but adopting a proactive security posture. This posture acknowledges the inherent risks, prioritizes data based on value, and employs a multi-layered defense strategy.
While absolute security may be a myth, building a robust security posture can significantly reduce the risk of breaches and minimize damage if one occurs. Here are the key pillars of this approach, expanded for a deeper understanding:
Imagine a castle with a moat, drawbridge, and heavily fortified walls. This layered approach is the essence of in-depth defense. It involves deploying a variety of security controls at different points within a system. Firewalls act as the first line of defense, filtering incoming and outgoing traffic. Access controls ensure that only authorized users can access specific data. Encryption scrambles data at rest and in transit, making it unreadable even if intercepted.
This layering creates redundancy. If one control fails, others can still impede attackers. Additionally, it makes a complete breach significantly more difficult. Hackers must bypass multiple layers, considerably increasing the time and effort required for a successful attack.
Security needs a"fire drill" mentality. We must assume a breach will occur and have a well-defined incident response plan in place. This plan outlines the steps to take upon detecting a breach, such as isolating compromised systems, containing the damage, notifying authorities, and restoring affected data. A well-practiced plan minimizes downtime, data loss, and reputational damage.
Security isn't a one-time fix; it's a continuous process requiring constant vigilance. This entails regularly scanning systems for vulnerabilities, updating software with the latest security patches, and educating employees about cybersecurity best practices. By continuously monitoring systems and fostering a culture of security awareness, businesses can significantly reduce the risk of successful attacks and ensure their data security remains robust and adaptive to evolving threats.
Integrating security considerations into every stage of the product or system development life cycle is crucial. Security features shouldn't be an afterthought bolted onto a finished product but should be an integral part of the design and development process from the very beginning. This proactive approach ensures that security is woven into the fabric of the system, providing a more robust, more resilient defense against potential threats.
In an era where data breaches are not a matter of if but when, businesses must adopt a proactive and holistic approach to data security. The question of how much data security is enough is not about reaching an endpoint but about creating a resilient and adaptive security posture. It's about balancing cost with risk, leveraging technology while addressing the human element, and continuously evolving to meet new challenges. In the end, the right amount of security is the amount that protects your business, your customers, and your reputation in an increasingly hostile digital landscape.

Recently, a significant data exfiltration event targeting Snowflake customer databases came to light, orchestrated by a financially motivated threat actor group, UNC5537. This group successfully compromised numerous Snowflake customer instances, resulting in data theft and extortion attempts. It's important to note that Mandiant's thorough investigation found no evidence suggesting that the cyber threats originated from Snowflake's own environment. Instead, every incident was traced back to compromised customer credentials.
In this blog post, we’ll dive into the key takeaways from Mandiant’s investigation. We’ll also share some actionable insight to bolster your data security – because staying alert and proactive is your best defense in safeguarding your organization’s data integrity.
The attacks primarily involved the use of stolen customer credentials, leading to unauthorized access and data theft.
Mandiant provided comprehensive threat hunting queries to detect abnormal and malicious activities, which are crucial for identifying potential incidents.
Given these findings, it's imperative forSnowflake users to bolster their security measures. Here are some critical steps:
As you reflect on the recent incidents, it’s crucial to reflect on the broader implications to your organization’s security. To ensure you are well-prepared and resilient against emerging threats, consider the following questions:
1. Are your current security measures sufficient to detect and prevent unauthorized access, especially from compromised credentials?
2. How often do you review and update your access controls and permissions? Is this easy to do for your business?
3. Do you have robust monitoring in place to detect unusual activities and high error rates in real-time?
4. What proactive threat detection strategies are you employing to identify potential issues before they cause significant damage?
By addressing these questions and strengthening your security posture, you can better protect your Snowflake environment from similar threats. If you're looking to enhance your data security capabilities or you are not confident in your answers to the above questions, consider investing in advanced data security software purpose-built for Snowflake. ALTR’s solutions offer comprehensive protection, continuous monitoring, and proactive threat detection to safeguard your valuable data assets.
Would you like to explore how our data security solutions can help you secure your Snowflake environment? Contact ALTR today to learn more and schedule a demo.

Data, its meticulous management, stringent security, and strict compliance have become pivotal to businesses' operational integrity and reputation across many sectors. However, the intricate maze of evolving compliance laws and regulations, as we discussed in a recent blog, poses a formidable challenge to data teams and stakeholders. This dynamic regulatory environment complicates the already intricate workflows of data engineers, who stand on the frontlines of ensuring data compliance, constantly navigating through a sea of changes to maintain adherence.
The landscape of data compliance has shifted from a mere checkbox exercise to a continuous commitment to safeguarding data privacy and integrity. The advent of stringent regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, among others, has escalated the stakes. Each regulation has its unique set of demands, and failure to comply can lead to severe repercussions, including substantial fines and a damaged reputation. A recent study from Drata found that 74% of organizations state compliance is a burden, and 35% spend 1,000 to 4,999 hours on compliance activities.
For data engineers, this presents an incredibly daunting task. They are tasked with the critical responsibility of ensuring that the data architectures they develop, the databases they oversee, and the analytics they perform are in strict alignment with a complex array of regulations that vary not only by jurisdiction but also by the nature of the data. This requires a vigilant eye on the ever-changing regulatory landscape, an in-depth understanding of each law, and a clear comprehension of its applicability to the data they manage. This constant state of monitoring and adaptation disrupts standard workflows, delays projects, and introduces a layer of uncertainty into data operations.
Amid these challenges, automation and scalable data security shine as beacons of hope, promising to alleviate the burden on data engineers and enable them to concentrate on their core tasks.
The critical process of data classification is at the heart of any robust data security and compliance strategy. It tackles the initial hurdle of deciphering which regulations apply to specific data sets by identifying and categorizing data based on sensitivity. Automating this foundational step ensures that data is consistently managed in line with its classification, simplifying the maze of compliance with regulations like GDPR and CCPA.
Dynamic Data Masking (DDM) emerges as a practical solution for the real-time protection of sensitive data, ensuring it remains accessible only to those with authorization. This tool is particularly pertinent to complying with regulations demanding strict data privacy and access controls, allowing data engineers to implement scalable data access policies without altering the actual data.
The continuous surveillance of database activities through Database Activity Monitoring is crucial for maintaining compliance. It enables the early detection of unauthorized access or anomalous data handling, which could indicate potential breaches or non-compliance. This tool is instrumental in keeping an audit trail, a prerequisite for many data protection regulations, ensuring any deviations from standard data access patterns are promptly addressed.
Tokenization is a formidable shield for susceptible data types, such as Personal Health Information (PHI) or Payment Card Information (PCI), often under stringent regulatory scrutiny. By substituting sensitive data with non-sensitive equivalents, tokenization significantly reduces the risk of data exposure. It eases the compliance burden by narrowing the scope of data subjected to the most stringent regulations.
Format Preserving Encryption (FPE) allows organizations to secure data while preserving its usability, an essential factor for operational systems bound by data protection regulations. FPE ensures encrypted data remains functional within applications without modification, thus supporting compliance efforts by safeguarding data without hindering business processes.
Integrating open-source tools for data governance facilitates a smoother compliance journey by automating and simplifying data management tasks. These integrations ensure consistent data handling practices, enhance data quality, and foster a comprehensive data governance framework capable of adapting to evolving regulations, thereby bolstering an organization's compliance posture in a scalable and efficient manner.
Navigating data compliance with automation and advanced data management brings significant benefits beyond mere regulatory adherence, enhancing operational efficiency and competitive positioning.
Automating compliance tasks liberates data engineers to concentrate on their core functions, significantly speeding up project timelines. Automation facilitates rapid adaptation to regulatory changes and maintains a constant state of compliance readiness, boosting productivity and enabling businesses to respond swiftly to market demands.
Implementing precise data classification and stringent access controls reduces the risk of errors and inconsistencies. This ensures a steady flow of accurate and reliable data through organizational pipelines, crucial for informed decision-making and maintaining operational integrity.
In today's data-sensitive environment, a strong reputation for data security and compliance can enhance customer trust and loyalty, offering a distinct competitive advantage. Demonstrable data protection meets regulatory requirements and fosters customer retention and brand differentiation, turning compliance into a strategic business asset.
While the ever-evolving landscape of compliance laws poses significant challenges, the path forward isn't about memorizing every regulation but about leveraging technology to create a culture of informed compliance. This allows data engineers to shift their focus from frantic firefighting to strategic data management, ultimately unlocking the true potential of the information they hold.

When talking to customers about data protection in Snowflake, a few things get a little mixed up with one another. Snowflake’s Tri-Secret Secure and masking are sometimes considered redundant with ALTR’s tokenization and format-preserving encryption (FPE) - or vice versa. What we’ll do in this piece is untangle the knots by clarifying what each of these is, when you would use each, and the advantages you have because you can choose which option to apply to each challenge you come across.
Snowflake’s Tri-Secret Secure is a built-in feature, and it requires that your Snowflake account is on the Business Critical Edition. Tri-Secret is a hybrid of the “bring your own key” (BYOK) and the “hold your own key” (HYOK) approaches to using customer-managed keys for the encryption of data at rest. [ProTip for the Snowflake docs: Tri-SecretSecure is essentially a brand name for the customer-managed keys approach, and if you read these docs understanding that, then these docs are a little clearer.] When you use customer-managed keys, there is often a choice between having to supply the key to the third party (Snowflake in this case) on an ongoing basis or only giving it when needed – BYOK and HYOK respectively. Snowflake effectively combines these approaches by having you provide an encrypted version of the key, which can only be decrypted when it calls back to your crucial management systems. So, you bring an encrypted version of the customer-managed key to Snowflake but hold the key that can decrypt it. Tri-Secret is used for the actual files that rest on disks in your chosen Snowflake cloud provider and is a transparent data encryption – meaning this encryption doesn’t require a user to be aware of the encryption involved. It protects the files on disk without affecting anything at run time.
Snowflake’s Dynamic Data Masking is a very simple yet powerful feature. This feature requires Enterprise Edition (or higher). When a masking policy is used to protect a column in Snowflake, at run time, a decision is made to return either the contents of a column or a masked value (e.g., a set of “****” characters). You can apply this protection to a column either directly as a column policy or via a tag placed on a column associated with a tag-based policy. When you need to ensure that certain individuals can never see the legitimate values in a column, then Dynamic Data Masking is a perfect solution. The canonical example is ensuring that the database administrators can never see the values of sensitive information when performing administrative tasks. However, there are slightly more complex instances of hiding information where masking falls short. You can easily imagine a circumstance where users may be identifiable across many tables by values that are sensitive (e.g., credit card numbers, phone numbers, or government ID numbers). You want users doing large analytics work to be able to join these objects by the identifiers, but simultaneously, you’re obligated to protect the values of those identifiers in the process. Clearly, turning them into a series of “***” won’t do that job.
This is where ALTR’s Tokenization and Format-Preserving Encryption (FPE) enter the story. We could spend hours parsing out the debate about if tokenization is a super class of FPE, vice versa, or neither. There are people with strong arguments on every side of this. We’ll focus on the simpler questions of what each feature is, and when it is best applied. First, let’s define what they are:
- Tokenization replaces values with tokens in a deterministic way. This means that you can rely on the fact that if there is a value “12345” in a cell and it’s replaced by the token “notin” in one table, then if you encounter that value in another table, it will also be “notin” each time it started as “12345.” So now you can join the two tables by those cells and get the correct result. A key concept here is that the token (“notin” in this example) contains no data about the original values in any way. It is a simple token that you swap in and out.
- Format-Preserving Encryption (FPE) is like tokenization since you’re also swapping values. However, the “tokens” in this case are created through an encryption process where the resulting value maintains both the information and its format. FPE might replace a phone number value of “(800) 416-4710" with “(201)867-5309.” Like the tokens, that replacement will be consistent so one can use it in joins and other cross-object operations. Unlike the tokens, these values are in the same “format” (hence the name and the phone number token looking exactly like a different phone number), which means they will be usable in applications and other upstream operations without any code changes. In other words, FPE won’t break anything; it only protects information.
ALTR has both Tokenization and Format-Preserving Encryption solutions for Snowflake, which are cloud-native and immensely scalable. In other words, they can both keep up with the insane scale demands of Snowflake workloads. The application-friendly FPE often seems like the only solution you need at first glance. However, there are reasons for choosing to use only Tokenization or perhaps both Tokenization and FPE in combination. The most common reason for going Tokenization only is due to regulatory constraints. Since the ALTR Tokenization solution can be run in a separate PCI scope, it gives folks the power to leverage Snowflake for workloads that need PCI data without having to drag Snowflake as a whole into PCI auditing scope. The most common reason we see folks run both Tokenization and FPE together is to stick to a strict least-privilege model of access. Since Tokenization removes all the information about the data it protects, some will choose to tokenize data while it flows through pipelines into and out of Snowflake and transform it to FPE while inside Snowflake to get the most out of the data in the trusted data platform.
Hopefully, it’s clear by now that the answer to the question “Which one of these should I use?” is: it depends. If you’re already on Snowflake’s Business Critical Edition, then using Tri-Secret Secure seems like a no-brainer. The extra costs involved are nominal, and the extra protection afforded is substantial. The real questions come when applying Snowflake’s Dynamic Data Masking and either or ALTR’s Tokenization and Format Preserving Encryption (FPE). Masking is a great option for many administrative use cases. If you’re not concerned about the user being able to do cross-object operations like joins and need to hide the data from them, then masking is easily the best choice. The moment there is the need for joins or similar operations, then ALTR’s Tokenization and FPE are the right places to turn. Picking between them is mostly a matter of technical questions. If you have concerns about application compatibility with the protected data, then FPE is your choice. If you want to keep the protected data away from the data platform, then Tokenization is the best option since FPE runs natively in Snowflake. And there are clearly times when you may have workloads complex enough that all of these can be used in combination for the best results. You’ve got all the options you could ever need for Snowflake data protection. So now it’s time to get to work making your data safer than ever.

On June 10, 2024, cybersecurity research and response firm Mandiant published its findings on the ongoing security investigation of stolen customer data. This news was first broken to the public about Ticketmaster and Santander Bank on May 31, 2024.
Mandiant reports, “Mandiant’s investigation has not found any evidence to suggest that unauthorized access to Snowflake customer accounts stemmed from a breach of Snowflake's enterprise environment. Instead, every incident Mandiant responded to associated with this campaign was traced back to compromised customer credentials.”
If there is any relief for Snowflake customers, it’s that Snowflake’s platform itself had not been compromised - which could have led to the exposure of more than 9,000+ customer data sets. Instead, Mandiant is reporting that 165 potential companies were exposed. Why is this good news? This means Snowflake is a safe platform to store and use your data. Like any other cloud-based service, you must take steps to protect your data beyond what the vendor does for you. Understanding what you can do to strengthen your defenses is crucial.

There are many ways to understand how to approach data security in cloud-based SaaS systems. We’ll borrow Gartner’s. The above diagram breaks down the responsibilities of the customer and vendor for IaaS, PaaS and SaaS. Snowflake fits best in the SaaS pilar, and Snowflake’s nine security responsibilities for data and systems are shown in green, indicating they are unaffected by this incident. The two responsibilities in blue, People and Data, remain under the control of Snowflake’s Customers.
Customers are responsible for what data they put in Snowflake, which users they allow access to this data, and how that access is controlled. But Snowflake does not entirely leave the People and Data responsibilities squarely on their customers. They recognize the importance of keeping data safe and have built industry-leading security and governance capabilities that they provide to customers of all sizes. From role-based access controls (RBAC) to dynamic data masking, network access restrictions, and more, Snowflake helps customers with the remaining two security responsibilities of People and Data.

So why did this data exposure happen if Snowflake is fulfilling its responsibilities and assisting customers with theirs? Managing People, Data, and security is challenging regardless of an organization’s size or maturity. This is where ALTR comes in.
ALTR is a Data Security Platform specifically designed to help customers with their two data security responsibilities. ALTR does two things to help customers manage their People and Data: automate and scale the powerful Snowflake-provided native security and governance capabilities mentioned above and extend Snowflake’s security capabilities with Active Security measures.

For the first part, ALTR can connect to your Snowflake, leverage data classification or Snowflake Object Tagging, and ensure that only authorized users can access data according to company policy. All this happens without writing a single line of code. Your data people don’t have to become security experts, and your security people don’t have to learn SQL. This does not replace the built-in Snowflake capabilities –it depends on them. Snowflake’s enforcement layer is still the engine for applying the advanced ALTR capabilities. This includes RBAC, dynamic data masking and row-access policies, to name a few.
ALTR also provides detailed information and reporting for data and infosec teams to prove they follow data access compliance rules and deliver that reporting in near real-time.
ALTR’s Active Security capabilities are used by Snowflake’s most sensitive and regulated business to ensure Snowflake is safe for PII, PHI, and PCI information. However, these capabilities are not limited to only large or mature businesses. Active Security can help a small or young company secure one row of customer data in Snowflake.
Active Security includes Database Activity Monitoring, Data Access Rate Limiting (Thresholding), and cell-level data protection in the form of encryption or tokenization.
Database Activity Monitoring adds near-real-time logging and alerting capabilities to Snowflake, where Snowflake logging can be delayed as much as four hours after access. ALTR can send data access logs in seconds to security teams for analysis and processing. This dramatic reduction of time is difficult to do at the scale of Snowflake but is necessary to keep the most sensitive data in Snowflake. Customers can be alerted in near-real-time, within seconds of access, to check if these accesses are valid or seem suspicious.
Data Access Rate Limiting, or Thresholding, is a patent-issued feature exclusive to ALTR which can stop data access in real-time, even with valid credentials. Customers can set a policy indicating how much data a particular user can consume in a period. Once a user reaches their limit, their access to that data is blocked.
No other data access is limited for that user, and no other users are impacted by a single user reaching their limit. Users can log in to Snowflake, but if the limit has been met for the day, no more data will flow to that user. When combined with ALTR’s Database Activity Monitoring, customers can be alerted instantly when a user has reached their limit and decide what to do with that user.

Cell-level data protection takes the same type of on-disk data protection that Snowflake provides with Tri-Secret-Secure (TSS) and extends it deeper into the data. The purpose of cell-level protection with encryption or tokenization is to remove the single-party risk of Snowflake holding the data and encryption keys by adding a second (or even third) party to the equation. In this way, compromising a Snowflake user account does not necessarily mean the data can be compromised, making Snowflake safer.
With ALTR’s tokenization or Format-Preserving Encryption Native App, the data or the keys to decrypt the data are stored outside of Snowflake. When authorized users request access to the plain text, Snowflake and ALTR interact in real-time to provide the plain text data. This operates at the scale of Snowflake and uses ALTR’s SaaS platform in the mix.

Customers should follow all recommended Snowflake security best practices for user accounts, such as multifactor authentication and network access limitations for user accounts. But sometimes that’s not enough.
In this case, we have a simple answer to the above question of how ALTR could have helped stop or limit the exposure.
1. Security teams were unable to see the data exfiltration in near real-time. They were limited to the default delays of up to four hours after the data had been stolen. Installing ALTR’s Database Activity Monitor into your Snowflake account and hooking up the output of ALTR’s real-time logs to your email, chat system or SIEM tool would have notified the business to investigate the user accounts immediately. “Why would someone from outside the country be accessing all our customer data at this time of night? We should investigate right away.”
2. Cell-level protection, like ALTR’s FPE Native App, would have rendered the data access useless as the accounts likely would not have been given access to the decryption keys. ALTR’s FPE Native app is format-preserving and deploys determinism – meaning an email will still look like an email, and the protected values remain operational downstream without your users needing to decrypt and see them in plaintext. This means as the bad actors ran SELECT statements over the data, they would have received encrypted data back without receiving the encryption key. This makes data exfiltration useless and is why having a two-party system of data security is so widely used because it's effective.
3. In the case the impacted user accounts did have access to the decryption key by compromising an elevated permission user, ALTR’s Thresholds could have been configured to do two things: alert in real-time when more than 100,000 rows have been accessed by a single user in 1hr for example, and then cut off access to that same data after 500,000 rows of data were accessed by a single user. The user would be authenticated to Snowflake and allowed to access the table, but no data would come out. That impacted user would then be in the ‘penalty box’ without the ability to decrypt information further.
Active Security is the best way to ensure sensitive data is safe in Snowflake no matter what happens. Active Security can detect and stop a breach, not just notify you. All three Active Security features are in GA and running in production across many Snowflake user accounts today. Our product and team focus on one thing only: safeguarding sensitive data.

We're thrilled to announce that ALTR's Snowflake native app, Format-Preserving Encryption (FPE), is now available on the Snowflake Marketplace. This marks a significant step forward in our mission to make data security seamless, efficient, and scalable for our customers. Let's dive into what this means for you.
Imagine encrypting your sensitive data without altering its original structure or format. That's precisely what FPE does. It transforms plaintext data into ciphertext while keeping the same format. For example, a phone number like "(800) 416-4710" might be encrypted as"(201) 867-5309." This means your applications and systems can continue operating smoothly without needing changes to handle encrypted data.
Traditionally, encrypting data involved a lot of headaches. On-premises systems were expensive, costing millions of dollars per license, and they introduced significant lag because of the back-and-forth calls between Snowflake and the on-premises servers. This not only slowed down your queries but also burned a hole in your pocket with monthly costs.
With ALTR's Snowflake Native FPE, all the encryption and decryption happen locally within Snowflake. No more external calls, no more lag—just fast, secure data processing. Plus, your data stays protected at rest within the Snowflake Data Cloud, ensuring it's always secure.
Snowpark, Snowflake's developer framework, provides the perfect environment for our FPE solution. It supports fully functional applications, enabling us to deliver powerful encryption directly in Snowflake. This means you get top-notch data protection without compromising performance or ease of use.
Here's why this is excellent news for you:
ALTR's FPE integrates seamlessly with our existing data access control and security solutions. This means you can easily implement and manage comprehensive data security through our SaaS platform, no-code interface, and automated policy enforcement.
You save millions in licensing fees and monthly operational costs by eliminating the need for on-premises appliances. Plus, faster query response times make your data operations more efficient.
FPE ensures that your sensitive data is always protected, even as you scale and evolve your data ecosystem. It's particularly beneficial for industries like financial services and healthcare, where maintaining data interoperability with legacy systems is crucial.
"ALTR's FPE offering running natively in our Snowflake environment proved to be far more effective, scalable, and affordable than the legacy solutions we considered. Further, with ALTR's cloud-native, SaaS architecture, we could extend FPE upstream into our data pipeline, expanding our compliance footprint to include a staging area prior to workloads landing in Snowflake."
Craig Hipwell, Customer Platforms Delivery Manager,Shell Energy Customer Platforms Delivery Manager,
With ALTR's FPE now available on the Snowflake Marketplace, you have all the tools you need to protect your data efficiently, effectively and at scale. It's time to take your data security to the next level.
Explore our FPE solution on the Snowflake Marketplace and see how easy it can be to keep your data safe while maintaining top performance.

I’ve spent the last two decades in enterprise software sales, where I’ve had the privilege of building and leading high-performance sales and marketing teams. My career has taken me from established, large-scale organizations to dynamic, ground-zero startups. Throughout this journey, I’ve successfully brought together all facets of Go-To-Market strategies under a cohesive team structure. My expertise lies in navigating complex ecosystems such as ServiceNow and Snowflake, where I’ve developed comprehensive market strategies that drive growth and success. I’ve consistently focused on aligning sales initiatives with broader business goals, ensuring sustainable revenue streams and long-term customer relationships.
Several factors influenced my decision to join ALTR. First and foremost, I was thoroughly impressed by the ALTR team. Their deep understanding of current data security challenges and their forward-thinking approach to simplifying and scaling data security stood out to me. Additionally, the opportunity to be at the forefront of the cloud data revolution is incredibly exciting. As businesses increasingly migrate their critical data to the cloud, they adopt advanced technologies like machine learning and artificial intelligence to gain competitive advantages. ALTR's dedication to helping clients balance this technological innovation with robust cloud data security makes it an inspiring endeavour to be part of.
My vision for ALTR is to establish us as the de facto standard for cloud data security. This involves offering a robust, rock-solid platform and leading the industry with unmatched security expertise. Under my leadership, I aim to drive the company past critical growth milestones typical for a thriving SaaS enterprise. This includes expanding our market reach, continuously innovating our product offerings, and maintaining a relentless focus on customer satisfaction. I foresee ALTR evolving into a cornerstone of data security, trusted by organizations worldwide to protect their most valuable asset: their data.
Over the years, data security and governance have undergone significant transformations. The landscape has evolved from simple perimeter defenses to sophisticated, multi-layered security strategies. Despite these advancements, cybercriminals continue to outpace many enterprises due to the high stakes involved. The fundamental principles of data security – knowing where your data is, who has access to it, and ensuring its protection – remain unchanged. However, in the next five years, the challenge will lie in meeting these requirements at the scale and speed of the cloud.
Building a successful software company hinges on four key pillars:
Product: It all starts with having a viable and innovative product that addresses real market needs. ALTR excels here with its scalable data security solutions tailored for the cloud era.
Market: Identifying and targeting an addressable market is crucial. The demand for robust data security and governance solutions grows exponentially as more businesses move to the cloud.
Defense: Defending your market position against competitors is essential. ALTR’s advanced technology, coupled with its deep industry expertise, provides a formidable defense.
Team: The most critical element is having a team that can build and execute together effectively. At ALTR, we have a dedicated, talented team committed to our mission of simplifying data security and data access governance.
These pillars make ALTR an exceptional solution for organizations seeking to enhance their data security and governance and make it an attractive place for top talent in the industry. By joining ALTR, professionals can work on the frontlines of data security innovation, contributing to solutions that make a real difference in today’s digital landscape.
.png)

For data engineers, there's a comforting hum in the familiar, a primal urge to build things ourselves."DIY is better," whispers the voice in their heads. But when it comes to data masking in Snowflake, is building policies from scratch the best use of our time?
Sure, the initial build of a masking policy might be a quick win. You get that rush of creation, the satisfaction of crafting something bespoke. But here's the harsh reality: that initial high fades fast. Masking policies are rarely static. Data evolves, regulations shift, and suddenly, your DIY masterpiece needs an overhaul.
This is where the actual cost of the"DIY is better" mentality becomes apparent. Let's delve into the hidden complexities that lurk beneath the surface of Snowflake's manual masking policies.
Ah, version control. The unsung hero of software development. But when it comes to DIY masking policies, it can be atangled mess. Every change, every tweak you make, needs to be meticulously documented and tracked. One wrong move, and you could be staring down the barrel of a data breach caused by an outdated policy.
Imagine the chaos if multiple engineers are working on the same masking logic. How do you ensure everyone is on the same page? How do you revert to a previous version if something goes wrong? While Snowflake recently announced a Private Preview for version control via Git, with a purpose-built UI like ALTR, version control is baked in and highly user-friendly. There is no need for complex terminal commands –just intuitive clicks and menus. Changes are tracked, history is preserved, and rollbacks are a breeze.
Snowflake offers a seemingly endless buffet of objects – a staggering 74 and counting, with new additions continually emerging. However, managing these objects poses a central challenge within the Snowflake ecosystem.
For instance, while masking policies reside within schemas, their impact extends far beyond. A single masking policy can be applied to tables and columns across numerous schemas within your Snowflake account.
This creates a masking policy headache. Choosing the correct schema for each policy is crucial, as poor placement leads to confusion and complex updates. Furthermore, meticulous documentation is essential to track policy location and impact. Without it, any changes or troubleshooting become a nightmare due to the potential for widespread, unforeseen consequences across your Snowflake environment.
With ALTR, you do not have to consider object management when masking policies. With our unified interface, you can easily create, edit, and deploy policies automatically in seconds, eliminating the need to navigate the intricate web of Snowflake objects and their relationships.
Data masking policies are living documents. As your data landscape changes, so too should your masking logic. New regulations might demand a shift in how you mask specific fields. A data breach requires you to tighten masking rules.
With DIY policies, every update becomes a time-consuming ordeal. You must identify the relevant policy, modify the logic, test it thoroughly, and then deploy the changes across all affected Snowflake objects. Multiply that process by the number of policies you have, and you've just booked a one-way ticket to Update City – population: you, stressed and overworked.
ALTR simplifies this process. Its intuitive UI allows for quick and easy changes to policies. Updates can be deployed across all relevant objects with a single click, eliminating the need for manual deployment across potentially hundreds of locations.
Let's not forget the critical step of validation. Every change you make to a masking policy must be rigorously tested to ensure it functions as intended. This involves creating test data, applying the new masking logic, and verifying that the sensitive data is adequately protected.
Imagine manually validating dozens of masking policies across hundreds or thousands of tables and columns. It's a daunting task, and relying solely on automated pipelines for testing adds another layer of complexity that needs ongoing maintenance. It's enough to make any data engineer break out in a cold sweat.
The benefits of ditching DIY masking policies extend far beyond just saving time. It's about empowerment. With ALTR's easy-to-use UI, even non-technical users can create and edit masking policies. This frees up valuable engineering time, allowing you to focus on more strategic initiatives. It also fosters a culture of data ownership and responsibility, where everyone involved understands the importance of data security.
Let's face it: the "DIY is better" mentality can be a trap in data masking. It might seem like a quick win initially, but the long-term costs – time, complexity, and risk – are too high. Embrace the power of purpose-built tools like ALTR. Free your engineering time, empower your team, and ensure your data is masked effectively and efficiently.
Ready to ditch the DIY trap? Schedule an ALTR demo.

Snowflake Arctic and the Future of AI Governance If you’re reading this, then it’s certain you saw the news about Snowflake’s Arctic model launch. Machine learning and AI is the next natural step for the Snowflake Data Cloud. Not only because it’s a hot trend, but because the Snowflake story naturally leads you to AI. What makes machine learning better? Lots of data. Where are you putting more and more of your data? Snowflake. Of course, there’s no such thing as a free lunch. While your data scientists, developers, and all the other Snowflake enthusiasts in your orbit are rushing to see how they can start leveraging Arctic (and there are already ways popping out of the Snowflake teams as well), maybe you’re here because you have accountability for your organization’s data. You may have one very important question: how is Arctic going to affect my governance and security stance? We’re here to answer that question, and the answer is mostly good – if you’re going to do the right things right now.
The TLDR on this is simple. Arctic is like every other thing that runs in the Snowflake Data Cloud. Nothing in Snowflake escapes the watchful eye of Snowflake governance policies. Nothing in Snowflake can skip past the network controls, security checks, encryption, or RBAC (Role-Based Access Control). The simplest way to understand this is that to use all this power in the Arctic LLM you have a list of simple, built-in Snowflake functions. You only have permission to use the AI stuff if you have permission to use those functions. And you only have permission to feed data that you are already allowed to access into those functions. Simple, right? End of the story, right? If that were the end, that would also be the end of this post. Honestly, I probably wouldn’t have bothered to write it if that were the case.
While it’s true that AI access is limited to the Cortex functions and that people will only be able to bring the data they already have access to into those functions, when you combine AI and the huge wells of data that Snowflake tends to have things may get weird. It’s not unusual for people (or services) to be over-provisioned. Just yesterday we were on the line with a prospect who was shocked to see ALTR’s real-time auditing picking up dozens of jobs running under the Snowflake SYSADMIN role. These queries running with too much privilege happened because lots of folks were granted this role through nesting to make it easier for them to get some data that had been put in a database that it probably shouldn’t have been in, and it was easier to grant the role than move the data. (This sort of security gap is exactly why this company is looking at ALTR in the first place!) With that SYSADMIN role, those users could have accessed tons of stuff they weren't supposed to. They didn’t (we know that because ALTR’s auditing would have caught them), but since they had the access, they could have. Humans tend to only query data they know they have access to. But what happens when AI takes the wheel?
Right now, the impact that AI’s power can have in Snowflake is limited. But just like having a model like Snowflake’s Arctic was the next natural step in the Snowflake story, there are more natural steps we can imagine. People are going to throw all the data they have at this thing to attempt to get amazing results. What happens when they have access to data they shouldn’t? What happens when they should have access to a table, but maybe there’s sensitive information in columns and there needs to be advanced data protection in place to make that data usable in the context of Cortex, Arctic, and AI in general? The machines won’t use the same approaches humans will (and vice versa). That’s why humans and AIs make such an effective team when things go right. But that also means these LLMs won’t limit themselves to only what they know. They will crawl through every scrap of data they have access to trying to find the right answer to get that good feedback we’ve programed them to seek. What happens when that machine is mistakenly given SYSADMIN role like the humans were? And, of course, people are going to build fully automated systems where the AI-powered machines will run all the time pushing these boundaries. Humans sleep, take time off, and eat a meal every now and then. What happens when your governance and security must be on watch 24/7 because they’re contending with machines that never step away?
The good news is that we’re only standing on the tip of this iceberg (pun intended). Most of this stuff is still a little while away. But as with everything else related to AI, it’s going to move fast. So now more than ever it's crucial that security and governance be integrated into the data and development pipelines and CI/CD approaches as well as automated as much as possible. Snowflake has all the controls you need to prevent the bad stuff from happening, but you need to use them effectively and automatically. The sensitive information in your data needs special attention more than ever in an AI-powered world. In that conversation yesterday, the customer asked about the new Arctic stuff and how ALTR could address that even though it just dropped this month. The answer is simple: ALTR has been in the proactive security business since the start. Since Snowflake did the right thing by building security directly into the Arctic and AI design, it’s just another thing ALTR can help you lock down as you roll it out. It all fits together perfectly. The next natural step in that company’s story – and maybe in yours – is to decide to let us help them out. We’re ready for AI when you are.